Connect both EAP and PEAP configured Users on the same Switch via ISE
Objective:Connect two machines at same time to allow them to authenticate using EAP-TLS and PEAP at the same time.

Objective:Connect two machines at same time to allow them to authenticate using EAP-TLS and PEAP at the same time.

Hello Team, I hope you are doing great, I have an external Radius Server (Secure W2 Radius), in which a have a Network Policy for Dot1x in which the only condition I have is NAS-Port-Type Ethern...

Umbrella offers a broad set of security functions that until now required separate firewall, web gateway, threat intelligence, and cloud access security broker (CASB) solutions. Umbrella DNS is resolv...

Zero Trust architecture is the new trend of Security Philosophy based on the principe, never trust and continuously verify trust, which means even if the user is authenticated and permitted to access ...

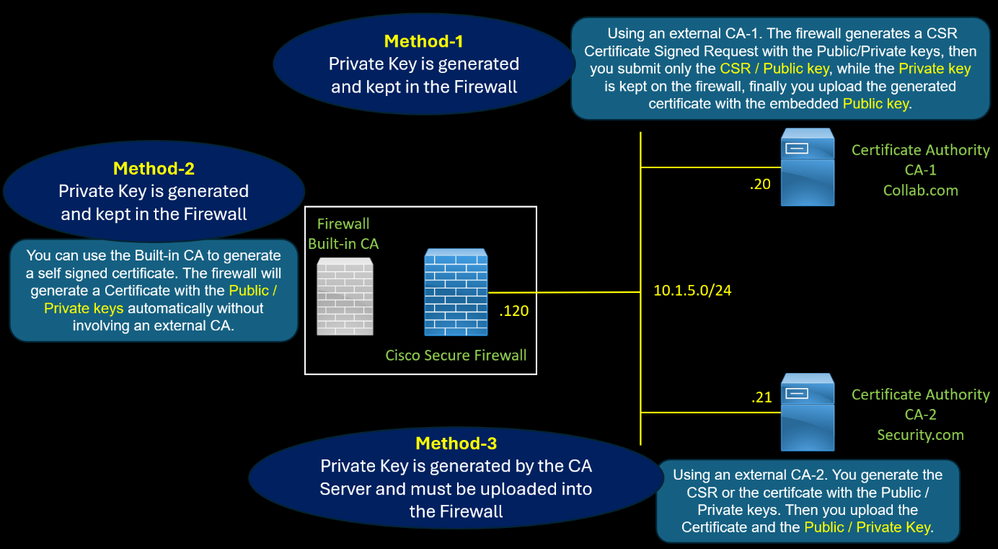
The firewall uses a certificate with the role of CA Certificate of Authority to perform SSL Decryption for outbound traffic. There are three methods to generate this certificate. Method 2 : Using a...
Unveiling the Future of Cybersecurity: Dive into a realm where AI transforms threat detection, response, and overall security posture. Explore dynamic use cases, from AI-driven anomaly det...

Cisco makes firewall management simpler than ever with Cisco AI Assistant.

Join the ranks of some of the best, brightest, and most passionate technologists. The 2024 Cisco Champion application is now open. Apply by January 12, 2024. As a Cisco Champion, you will: Get ea...

If you've heard about Private Keys but arent sure what they are read this! If you think you've seen large numbers before... are they THIS big?


AI Security Summit - November 30, 2023 If you are reading this is because you are interested in cybersecurity and artificial intelligence (AI). It has never been more crucial to discuss AI security....

Cisco SecureX is a cloud-native incident and threat response platform that aggregates third-party security platform APIs and the Cisco Security portfolio including Umbrella. In SecureX, you can respon...

Recently, I've received numerous inquiries regarding Retrieval-Augmented Generation (RAG) — what it entails and the advantages it offers. Additionally, I have been using and demonstrating the power of...

Web Policy Rulesets Rulesets are “containers” for rules. A Web policy ruleset defines a collection of identities and rules. Rulesets can include identities from a specific geographic area or physical ...

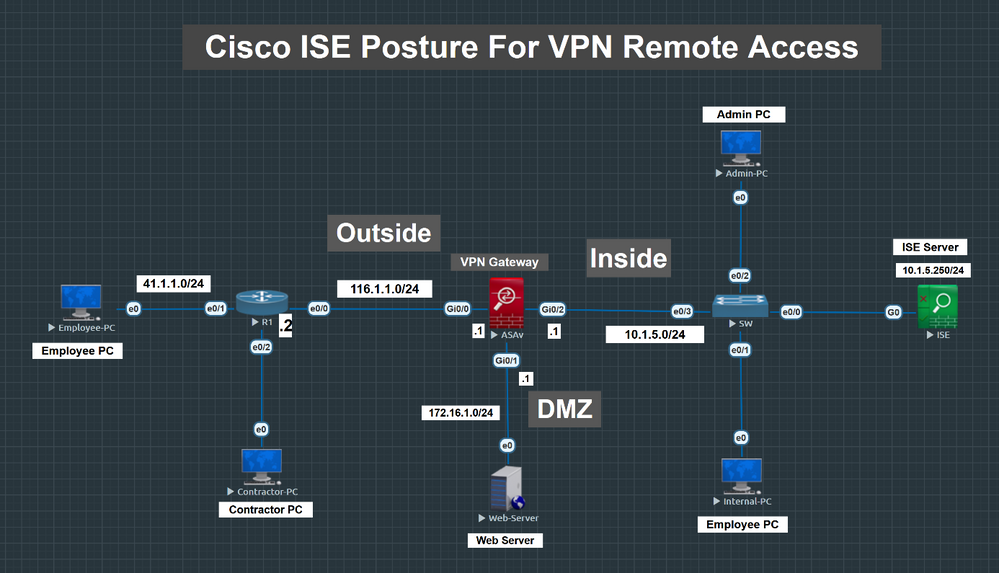
Step 1: Configure posture conditions Windows Assets can be marked as ‘Compliant’ when: Windows update agent is runningAny Firewall product is runningAny Anti-Malware software is installed Create a co...