- Cisco Community
- Technology and Support
- Security
- Other Security Subjects
- 3750 switch not forwarding EAPoL to RADIUS server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2010 08:47 AM - edited 02-20-2020 09:42 PM
I have a 3750 switch stack running version 12.2(53)SE2 IPBASEK9-M. I have dot1x configured on the switch and have a Windows 7 PC connected with 802.1x configured on the interface. I see the EAPoL start message from the PC, but I don't see any RADIUS packets from the switch to the RADIUS server. I have a simple dot1x config just to try to get it working prior to adding additional features such as guest-vlan...
Config and debug file attached.
I don't know if the ip dhcp snooping and arp inspection configuration is causing an issue with this or not. I see the EAPoL packet received on the switch as seen in the debug attachment, but I still never see the RADIUS packet. I did set both to trust on the interface but still the same outcome. I can't disable it since it is a production switch with a test interface.
Any ideas?
Thanks,
Mark
Solved! Go to Solution.
- Labels:
-
RADIUS
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 01:10 AM
I got the same problem and simply solved by configure the switch as authenticator instead of supplicant. "Supplicant" means client, "authenticator" actually means the switch is acting as a pass-through authenticator, it will forward requests to the auth server, for e.g., radius host.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2010 03:34 AM
Hi Mark,
The config seems to be OK, nothing I would miss if I assume that mandatory
commands not shown in your config are in place
aaa-new-model is required for dot1x to function, I don't seee that command.
I have configured dot1x just a few times but I always used the commands
aaa authorization network default group radius
and
radius-server vsa send
(honestly, I'm not sure whether they are required, it's just a template which
I know as working)
Careful if this is a production system
AAA New-Model will radically change every authentication behaviour on the
switch if it is not already configured
The main issue seems that the catalys is not sending an "EAP-Request/Identity"
back, Radius-Packets will only be sent after the "EAP-Response/Identity":
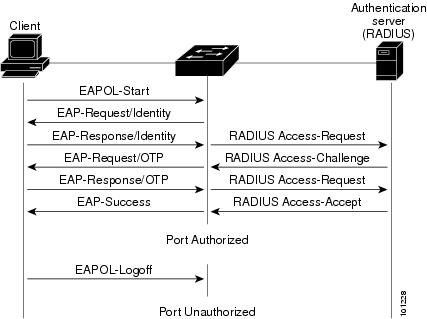
Do you have any other dot1x client?
You can use a cisco router for testing dot1x if you have
test system at hand:
conf term
dot1x credentials DOT1XTEST
username testuser
password testpassword
exit
interface [name-of-interface-connected-to-catalyst]
dot1x pae supplicant
dot1x credentials DOT1XTEST
Another approach:
use the classic config (not auth-manager but "dot1x syntax") you are
using a very new version of IOS, might be buggy:
Switch(config)# aaa new-model
Switch(config)# aaa authentication dot1x default group radius
Switch(config)# aaa authorization network default group radius
Switch(config)# radius-server host [IP-address] auth-port [port] key [port]
Switch(config)# dot1x system-auth-control
Switch(config)# interface [interface]
Switch(config-if)# switchport mode access
Switch(config-if)# dot1x port-control auto
Hope something is helpful
Additional debug hints:
use
show dot1x all
show dot1x interface [interface-name] detail
show dot1x interface [interface-name] satistic
Do see something like "RxResp = x" with x>0?
rgds, MiKa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2010 04:43 AM
m.kafka,
Thanks for your response. I haven't seen the EAPOL request/identity being sent from the switch after receiving the EAPOL START packet. I do see the EAPOL request/identity sent from the switch when I manually forced the switch to check the dot1x capabilities with the dot1x test eapol-capable interface command. I see that the Windows 7 supplicant is sending version 1 packets and the switch is sending verion 3 packets. I don't see a response from the switch when the PC sends the EAPOL START and I don't see a response from the PC when the switch sends the manual EAPOL REQUEST/IDENTITY. I wonder if there is a compatibility issue between versions 1 and 3. Show dot1x on the switch shows it as version 3. I don't see how to change the dot1x version on the switch to test for compatibility issues.
When I issue the dot1x interface show commands on the switch I get no output at all. I may downgrade the switch to see if it works in an older IOS version.
Thanks,
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2010 04:49 PM
Hi Mark,
that issue seems to go a bit deeper than I have experience (compatibility issues and possible SW-bugs).
May I suggest to try the Cisco supplicant (cisco secure services client)? Just as an option...
rgds, MiKa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 01:10 AM
I got the same problem and simply solved by configure the switch as authenticator instead of supplicant. "Supplicant" means client, "authenticator" actually means the switch is acting as a pass-through authenticator, it will forward requests to the auth server, for e.g., radius host.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-22-2011 05:38 AM
Peng,
That was it. I don't recall needing that command when I looked at 802.1x a few years ago. I thank it just defaulted to authenticator then. I also didn't see that command in he documentation I was using.
I appreciate the reply. I had put that projecton the back burner after I started this discussion and hadn't really looked into it since. After getting your reply, I had it up and running in 5 minutes with another hour or so tuning the timers to alow for unauthenticated user to get on the guest VLAN prior to their laptop before DHCP timed out and it started using a local link IP of 169.254.x.x.
Thank you,
Mark
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
