- Cisco Community
- Technology and Support
- Security
- Network Security
- Passive FTP through a 877 to natted ip address on an ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2010 11:11 PM - edited 03-11-2019 11:32 AM
Hi there,
I am having some difficulty getting ftp transfers working the following scenario:
Computer sitting behind an 877 (that allows ports 20 and 21) on the wan connecting to an ip address on the wan interface of an ASA, which redirects to a Windows 2003 IIS FTP site on the LAN. There is no explicit natting on the 877 - just acls allowing ftp and ftp-data.
I can connect to the ftp site and authenticate - but when I try to list or upload data I get connection timeouts.
I realise that in most implementations extra ports need to be opened for static natting - as I'm not using nat on the WAN side what can I do to eliminate my issue?
Appreciate the help and advice.
Cheers
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2010 09:02 AM
Hey Greg,
Unfortunately too much of the config has been wiped off clean. I cannot really see what is wrong. Please just replace your public IPs alone with some imaginary ones when attaching configs and remove the passwords. Leave the private IPs as it is as they do not make a difference. Please do this and attach the config again.
But as i said in my previous post, try modifying the ACL on the 877 to allow all TCP traffic and also using Active FTP too if possible.
Regards,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2010 11:32 PM
Hi,
So i am assuming your topology is something like below:
SERVER-------(LAN)ASA(WAN)---------877---------client
You have a STATIC translation on your ASA which redirects requests to the server. Is it a PAT or a NAT? Can you paste the configuration on the ASA here? Also, since you are using passive FTP, the client will connect to the server not on TCP port 20 for the data connection but on some random port specified by the server. Please refer to the below document for more details:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00807ee585.shtml
On the ASA as well, you will need to have inspection enabled for FTP as below:
On the 877, you can add an ACL allowing all TCP traffic to the FTP server's NATed ip address. This should not be a problem or a security hole as you will be denying traffic on the ASA anyway. Let me know if this helps.
All the best!!
Regards,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2010 12:18 AM
Hi Prapanch,
your line diagram is right - the 877 and the client behind it are on a different segment of the WAN.
There is a static translation on the ASA redirecting to the ftp server on the LAN. It is using PAT (tcp) - original port is ftp, translated port is ftp. I've attached a screen shot of the nat rule.
Under Service Policy Rules the "inspection_default" policy has "inspect ftp" rule action checked.
On the 877 I have the following acls (allow ftp across the WAN, rather than one ip):
access-list 102 permit tcp 10.0.0.0 0.255.255.255 eq ftp 10.0.0.0 0.255.255.255
access-list 102 permit tcp 10.0.0.0 0.255.255.255 eq ftp-data 10.0.0.0 0.255.255.255
access-list 103 permit tcp 10.0.0.0 0.255.255.255 eq ftp any
access-list 103 permit tcp 10.0.0.0 0.255.255.255 eq ftp-data any
Should I create specific acls to address the issue or have I missed something else?
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2010 12:52 AM
Hi,
Can you attach the current configuration of the ASA after removing the IP address and password details? I think to be able to get this working, you will need to have a NAT for the server on the WAN_DMZ interface. The reason for that is as below:
Assuming your client IP address is 1.1.1.1. The WAN_DMZ interface ip address is 2.2.2.1 and the inside server's IP address is 3.3.3.1. based on the PAT that you have, this is how it is going to look:
TCP 3.3.3.1:20 on the inside is translated to appear as 2.2.2.1:20 on the WAN_DMZ interface.
Now, since we are using passive FTP, both the control connection and data connection are going to be client initiated. The control connection will be from a random port > 1023 on the client to server port 20. In this control channel is where the data port on the server is going to be specified by the server using the PORT command. Assuming the server says the PORT is going to be 2024 as below:
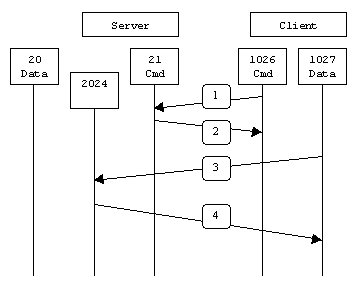
Now the client is going to try to connect to the server on port 2024 from a random port on it's side (and not on port 20) for the ftp data. hence, we need 2 things on the ASA:
1) an ACL on the ASA allowing this data connection.
2) a translation rule to redirect tcp 2.2.2.1:2024 on WAN_DMZ to 3.3.3.1:2024 on the inside interface.
Now 1) is going to be taken care of by the "inspect ftp" command.Please refer to http://www.cisco.com/en/US/docs/security/asa/asa82/command/reference/i2.html#wp1744171.
but, 2) will not be taken care of by the ASA. We will need to create a rule manually for that which is not possible because everytime the port that the server is going to specify will be different, that is, this time it was TCP 2024, next time it might be TCP 3057 or something random like that (decided by the server).
Now instead of the PAT on port 20 as above, if we have a NAT for the serve in the form below:
IP 3.3.3.1 on the inside interface is translated to 2.2.2.2 on the WAN_DMZ interface.
Now 2) is also automatically taken care of because of this STATIC mapping.
Coming to the ACLs on the 877 router, again as I explained before, just allowing ftp-data (TCP port 20) is not going to be sufficient as the FTP data port is going to be specified randomly by the server everytime. hence, you will need to allow all TCP connections on the router which should not be a problem as the we can always block what is necessary on the ASA.
Another thing you can try is try using Active FTP if possible and see if that works from the client to the same server.
Let me know if this helps.
Regards,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2010 01:16 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2010 09:02 AM
Hey Greg,
Unfortunately too much of the config has been wiped off clean. I cannot really see what is wrong. Please just replace your public IPs alone with some imaginary ones when attaching configs and remove the passwords. Leave the private IPs as it is as they do not make a difference. Please do this and attach the config again.
But as i said in my previous post, try modifying the ACL on the 877 to allow all TCP traffic and also using Active FTP too if possible.
Regards,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2010 03:06 AM
Hi Prapanch,
added the acls correctly and ftp is working properly - many thanks for your help!
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2010 07:38 AM
Hey Greg,
Glad to know that. All the best!!
Cheers,
Prapanch
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
