- Cisco Community
- Technology and Support
- Networking
- Routing
- Ospf inter area filtering problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ospf inter area filtering problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2011 09:10 PM - edited 03-04-2019 12:58 PM
hi,
i have two core router one is DC end and another is DR end. every branch office is connected to this two routers. DC and DR router also connected through a vendor. my requirement is when the connection between DC and DR failed then i dont want that DC local lan reach the DR local lan through branch routers which means that the branch acts as a transit path. in this case DC and DR local lan dont need any communication. i have a solution about distribute list but it should be set in every tunnel interfaces which is very much cumbersome for my scenario. if anyone have any suggestions then please share with me. i also attached a diagram below............
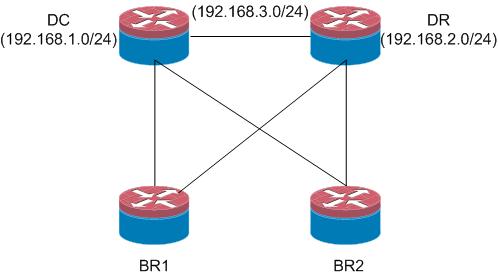
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2011 09:52 PM
Ahmed,
If you can post your OSPF logical topology showing Area layout it will be easier for us to provide an accurate response. Depending on how the Area layout is what you want can be met automatically by OSPF. For example if the DC and DR routers are ABRs and the branch area is different than the DC/DR LAN area then DC to DR LAN traffic will not traverse the branch area.
Atif
Ahmed Chowdhury wrote:
hi,
i have two core router one is DC end and another is DR end. every branch office is connected to this two routers. DC and DR router also connected through a vendor. my requirement is when the connection between DC and DR failed then i dont want that DC local lan reach the DR local lan through branch routers which means that the branch acts as a transit path. in this case DC and DR local lan dont need any communication. i have a solution about distribute list but it should be set in every tunnel interfaces which is very much cumbersome for my scenario. if anyone have any suggestions then please share with me. i also attached a diagram below............
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2011 11:38 PM
Hi
as mentioend by the above poster we need somthing to show your OSPF Areas
but if the route is coming over the branches when the link between the DR and DC is down then there is either virtula links
or you have the the link between the branches and DR DC in one area and link between DC DC in Area 0
if the above is the case then just use ospf filter-list to filter out LSA type 3 from barnches area to come in to the DC router
good luck
if helpful Rate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2011 01:55 AM
hi marwan,
you are right. my DC, DR are in area 0 and each br has a unique area id but my all branches are not connected directly each other. they all are connected through my DC and DR router. so i have to use ospf filter list command on my DC, DR router to prevent the branches which act as a transit area, when the DC, DR link failed. correct me if i am wrong..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2011 04:16 AM
That's right
Int dc filter the dr sinners and in the dr filter the dc subnets from coming from br areas
Good luck
Please rate the helpful post appropriately
As you rated the last one as not helpful !
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2011 06:26 AM
Provided the explanation of the topology is correct and Area 0 remains contiguous after the DC to DR link failure your DC to DR traffic will stay within Area 0 without any need for any filters. If your topology is such that there is no resiliency on your Area 0 interconnect and after DC to DR link failure both DC and DR have no neighbors left in Area 0 then there is potential of DC to DR traffic transiting the branch Area. In this case if I were you I would look at adding resiliency to your backbone Area.
Atif
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2011 04:02 PM
what Atif motioned above it Correct,
once you have the link between the DC and DR down you will have a split Backbone area ( area 0 ) in this case route in area 0 will no go over a non area 0 to area 0 again which means in normal cases you do not need to do anything as OSPF areas ( as per your mentioned topology ) will take care of this issue
however if you tested it and you have the route still going over the branches back to the DC/DR then i think you have a back interface in area 0 either a virtual link or a tunnel interface gose over the branches and this interface is leaking the route
filter-list will dose the job of LSA 3 filtering
however for more scalable and best practice design you can put the branches in totaly Stubby area or totally NSSA ( if you have any redistributed route in the branches ) having said that be careful if you have any local default route/Internet in the branches
hope this help
if helpful rate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2011 08:35 PM
hi marwan,
you are right my dear. my all branches are connected to this DC and DR through Tunnels. thats why when my DC, DR link failed then DC, DR lan reaching each other using the branches Tunnel interfaces as a transit. i already applied a filter-list for all of my branches to receive only the DC, DR local lan. now i have to apply another filter-list in DC, DR router to prevent the branches which acts as a transit. i am already done this but there is no luck. if u have any further suggestions then pls let me know. i want to add that i already got a solution using distribute-list but it is much more cumbersome bcoz in this case i have to apply the distribute-list in every tunnel interfaces and i have atleast 400 tunnels, and i dont want to go in this way.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2011 09:35 PM
Hi Ahmed
can you confrim if the Tunnel intrerfaces are in area 0
also why you have those tunnels are using any multicasting for example not supported by the ISP
anyway is the above it right then with filter-list might block it from bing injected to area 0 but still your router can see the route right ?
from the number of tunnels it is hard to re design your OPSF areas as it is better to do so but i dont thin this is an option fo ryou now
what about if you try some work arounds for example you do not want your DC router to reach the DR over the braches when the link between them is down
for example use the bellow method to filter out the DR subnet if it sourced from any next hop other than the DR
DR LAN 192.168.2.0/24
DR IP 192.168.3.2
DC Router :
router ospf 1
distribute-list route-map ROUTE_FROM_DR in
!
access-list 3 permit host 192.168.3.2
!
access-list 34 permit host 192.168.2.0
access-list 38 permit host 192.168.2.0
access-list 38 deny any ----- this ACL will be use din the deny seuenc eof the route-map bellow to make sure if the DR is down the route of 192.168.2.0 will be denied ( route-map deny ) and other routes will be allowed ( excluded from this route map deny sequence )
!
route-map ROUTE_FROM_DR permit 10
match ip address 34
match ip next-hop 3
!
route-map ROUTE_FROM_DR deny 30
match ip address 38
route-map ROUTE_FROM_DR permit 80
please be careful whe nyou try it as i did not test it in a lab
if dose work you can then apply the same idea in the the DR for the DC subnet
good luck and let meknow if worked for you or not
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 12:05 AM
hi Marwan,
i applied it to my lab. when my DC, DR link failed then in my DC routing table there is no information about DR lan but still i can ping my DR lan through my branches(using ospf default routes). heres my DC router routing table ::
Gateway of last resort is 10.3.3.2 to network 0.0.0.0
172.16.0.0/24 is subnetted, 2 subnets
O 172.16.1.0 [110/2] via 10.1.1.2, 00:06:22, FastEthernet1/0
O 172.16.2.0 [110/2] via 10.3.3.2, 00:06:22, FastEthernet2/0
10.0.0.0/24 is subnetted, 4 subnets
O 10.4.4.0 [110/2] via 10.3.3.2, 00:06:22, FastEthernet2/0
C 10.3.3.0 is directly connected, FastEthernet2/0
O 10.2.2.0 [110/2] via 10.1.1.2, 00:06:22, FastEthernet1/0
C 10.1.1.0 is directly connected, FastEthernet1/0
192.168.1.0/32 is subnetted, 1 subnets
C 192.168.1.1 is directly connected, Loopback0
O*IA 0.0.0.0/0 [110/3] via 10.3.3.2, 00:02:16, FastEthernet2/0
[110/3] via 10.1.1.2, 00:02:16, FastEthernet1/0
DC#
i want that when my DC , DR link will fail then there will no communication between DC and DR local lan. but thank u very much brother for your help. if you have any further suggestions then please let me know.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 01:04 AM
Hi Ahmed,
Suposing that you originate the default route only from DR and DC, and from branches you originate only LAN prefiexs, I would try using "gateway" option on distribute list together with "interface" on the DC router.
distribute-list prefix Lan-1 gateway Branch-1 in FastEthernet2/0
ip prefix-list Lan-1 permit
ip prefix-list Branch-1 permit 10.3.3.2/32 <<<< if this is the next-hop to the Branch
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 01:36 AM
hi Dan,
i applied this method. but there is no luck.. by this time i have fix this problem by filtering the default route.
Thanks..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 01:23 AM
Hi Ahmed,
can you please explain your default route
where its generated from
how it supposed to be working the case the link between the DC and DR is up and when its down ? and dose the braches uses this default route ?
than i can help you to overcom this issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 01:42 AM
hi Marwan,
i solved this issue by filtering the default route. here's the solution::
access-list 38 permit 0.0.0.0 0.0.0.0
by doing this my DC lan cant access to my DR lan in the event of DC, DR link failure. Thank u very much marwan. thanks a lot.....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 01:48 AM
Perfect
this is one of th eoption i was thinking to tell but i wanted to confirm this will not break your default routing first
as long as this will not break your default routing in the DC or DR then its good
plz rate the helpful posts and Good luck
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

