- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Knowledge Base
- Chalk Talk: An Insight into Cisco IP Telephony Security Controls
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-03-2012 08:09 PM - edited 03-12-2019 09:53 AM
It’s only natural to think about the security of your network or a network you have designed or deployed. Cisco IP Telephony networks are no different, and they need their share of security to ensure that things work out the way you planned them and not how an attacker plans them to work for his motives. With that said, it always comes as a surprise that security is not one of the first topics discussed when an IP Telephony network is planned or designed.
Why you may ask? For a few reasons: perhaps there is a lack of confidence to secure a relatively (compared to data networks) technology, or maybe it’s a scarcity of resources (monetary or manpower) or management support.
Let’s say you are able to overcome these initial hurdles when preparing, planning, and designing security for your Cisco IP Telephony network; are you sure what you have put down in the plan or design is the right set of security controls to help you ensure the sanctity and stability of Cisco IP Telephony solution? Are you confident that the security you planned aligns well with your organization’s vision/goals? This article helps you answer these questions by exploring the security controls that help you to plan for and implement security for your Cisco IP Telephony solution.
Security Control – What is it all about?
To begin with, let’s understand what a security control is. An information technology (IT) security control can be described in two ways. It could be a physical control applied somewhere in the network to deter attacks or an attempt to initiate an attack. It could also be described as a control logically applied to restrain attacks. In a nutshell, it is a logical or physical control that can be applied at various network layers to ensure that the attacks directed towards Cisco IP Telephony applications, endpoints, underlying infrastructure, or servers can be curbed. On the same note, security controls can be very powerful, provided they are well thought out and planned well as to where a control is required and should be applied.
There are 3 major types of security controls based upon the actions a security control can take:
- Detective
- Corrective
- Preventive

Figure 1: Overview of Cisco IP Telephony Security Controls
Detective security controls can be compared to a security alarm; that is, they detect and report an undesired event after the attempt to attack or the attack itself has taken place. Examples include log monitoring, system audit, and motion detection.
Corrective security controls are used to respond to and fix a security incident, after the incident has occurred. Examples include Antivirus to clean a virus from an infected system or to update edge router's ACL's to block an attacking IP address.
Preventive security controls are helpful to prevent intentional or unintentional disclosure, alteration, or destruction of sensitive information. A fine example of preventive control is that of Intrusion Prevention System (IPS), which could be Network IPS (NIPS) or Host IPS (HIPS), that can detect malicious packets and can stop the attacker in its tracks.
It is important to note that a single security control (physical or logical) might not fare well against a flurry of attacks. To achieve an end-to-end security, the defense-in-depth approach must be adopted. In other words, a layered security approach helps deter a multitude of attacks, even if one of more security control has been overwhelmed (bypassed or bungled) by an attacker. Figure 2 depicts an overview of the defense-in-depth approach leveraging multiple layers of security controls at various network layers.

Figure 2: End-to-end Cisco IP Telephony Security Construct (Leveraging Multiple Layers of Security Controls)
With the background of security controls explained, let’s look into Cisco IP Telephony specific security controls that you can plan for and implement to ensure that your Cisco IP Telephony design or deployment phase(s) include security as de-facto standard.
Cisco IP Telephony Security Controls
A Cisco IP Telephony network is not a single construct; however, it’s made of various components that work together to deliver a world-class user (and administration) experience. These components can be broadly classified as:
- Physical Security – which includes all mechanisms to prevent physical removal or sabotage of servers or devices from premises
- Underlying network infrastructure – which includes (but is not limited to) Cisco Catalyst switches, Cisco IOS routers, etc.
- Network Perimeter – which includes Cisco ASA Firewall and Cisco NIPS
- Cisco IP Telephony applications – which includes (but isnot limited to) Cisco Unified Communications Manager, Cisco Unity Connection, Cisco Unified Communications Manager Express, Cisco Unity Express, Cisco Unified Presence, etc.
- Cisco IP Telephony endpoints – Cisco IP Phones (wired and wireless), Cisco soft phones
- Cisco IP Telephony gateways and SBC’s – Cisco voice gateways, Cisco Unified Border Element
Let’s look at various security controls pertinent to the categories defined earlier. Please note that the security controls defined in this document are the most common and widely used security controls and do not represent a comprehensive list of security controls. Moreover, not all security controls are relevant for all networks as no two networks are alike. Therefore, it’s strongly recommended that you research which of the defined controls in this document or otherwise are applicable to your network.
Cisco IP Telephony Physical Security Controls
Table 1 lists the various security controls and their respective logical or physical nature, along with the type (corrective, detective, or preventive) for physical security.
Table 1: Cisco IP Telephony Physical Security Controls

Table 2 lists the various security controls for underlying network infrastructure components.
Table 2: Cisco IP Telephony Network Infrastructure Security Controls

Table 3 lists the various security controls for perimeter security.
Table 3: Cisco IP Telephony Network Perimeter Security Controls

Cisco IP Telephony Application Security Controls
Table 4 lists the various security controls for Cisco IP Telephony applications.
Table 4: Cisco IP Telephony Application Security Controls


Cisco IP Telephony Endpoint Security Controls
Table 5 lists the various security controls for Cisco IP Telephony endpoints.
Table 5: Cisco IP Telephony Endpoint Security Controls
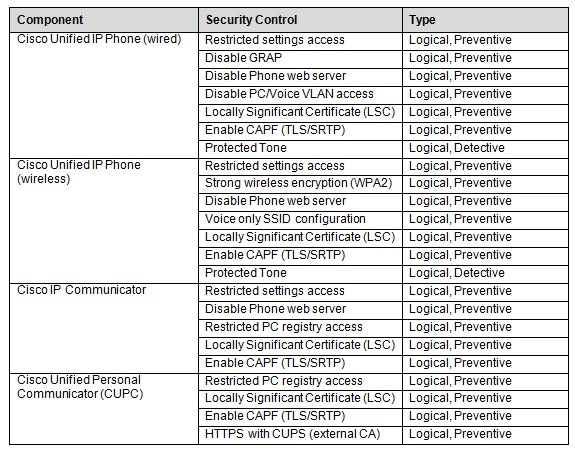
Cisco IP Telephony Endpoint Security Controls
Table 6 lists the various security controls for Cisco gateways and Cisco Unified Border Element.
Table 6: Cisco IP Telephony Gateway and CUBE Security Controls

Summary
It’s your Cisco IP Telephony solution, and there’s no reason why anyone rogue should be able to get his hands on it. An end-to-end security construct comprised of security controls at multiple layers is what stands between the bad guys with good guns and your network. While hundreds of security controls are available to help secure sensitive information, you really need to chalk out which ones are relevant to your network and how you plan to leverage them. The intent of this article was to outline the diverse security controls pertinent to Cisco IP Telephony network, classified as logical, physical, preventive, corrective, and detective with the intent to help you discover various security controls, which you can implement when deploying the solution or integrating it in design phase.

Akhil Behl, CCIE No. 19564, is a Senior Network Consultant with Cisco Services, focusing on Cisco Collaboration and Security Architectures. He leads collaboration and security projects worldwide for Cisco Services and the Collaborative Professional Services (CPS) portfolio for the commercial segment. Prior to his current role, he spent ten years working in various roles at Linksys as a Technical Support Lead, as an Escalation Engineer at Cisco Technical Assistance Center (TAC), and as a Network Consulting Engineer in Cisco Advanced Services. Akhil has a bachelor of technology degree in electronics and telecommunications from IP University, India, and a master’s degree in business administration from Symbiosis Institute, India.
Akhil is a dual Cisco Certified Internetwork Expert (CCIE) in Voice and Security. He also holds many other industry certifications, such as Project Management Professional (PMP), Information Technology Infrastructure Library (ITIL) professional, VMware Certified Professional (VCP), Information Security Management, and Microsoft Certified Professional (MCP). Over the course of his career, he has presented and contributed in various industry forums such as Interop, Enterprise Connect, Cloud Connect, Cloud Summit, Computer Society of India (CSI), Cisco Networkers, IT Expo (West), and Cisco SecCon. He has several research papers published to his credit in various international journals.
 | Securing Cisco IP Telephony Networks By Akhil Behl ISBN-10: 1-58714-295-3ISBN-13: 978-1-58714-295-6 Published: August 31, 2012 US SRP: $55.99 Published by Cisco Press |
This article was featured in the October issue of the Cisco TS Newsletter. Are you subscribed?
Physical Security – which includes all mechanisms to prevent physical removal or sabotage of servers or devices from premises
Underlying network infrastructure – which includes (but is not limited to) Cisco Catalyst switches, Cisco IOS routers, etc.
Network Perimeter – which includes Cisco ASA Firewall and Cisco NIPS
Cisco IP Telephony applications – which includes (but isnot limited to) Cisco Unified Communications Manager, Cisco Unity Connection, Cisco Unified Communications Manager Express, Cisco Unity Express, Cisco Unified Presence, etc.
Cisco IP Telephony endpoints – Cisco IP Phones (wired and wireless), Cisco soft phones
Cisco IP Telephony gateways and SBC’s – Cisco voice gateways, Cisco Unified Border Element

Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: