- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- How to configure a GRE tunnel
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-22-2009 03:34 PM - edited 03-01-2019 03:49 PM
Introduction:
Tunneling provides a mechanism to transport packets of one protocol within another protocol. The protocol that is carried is called as the passenger protocol, and the protocol that is used for carrying the passenger protocol is called as the transport protocol. Generic Routing Encapsulation (GRE) is one of the available tunneling mechanisms which uses IP as the transport protocol and can be used for carrying many different passenger protocols. The tunnels behave as virtual point-to-point links that have two endpoints identified by the tunnel source and tunnel destination addresses at each endpoint.
The below diagram shows encapsulation process of GRE packet as it traversers the router and enters the tunnel interface:
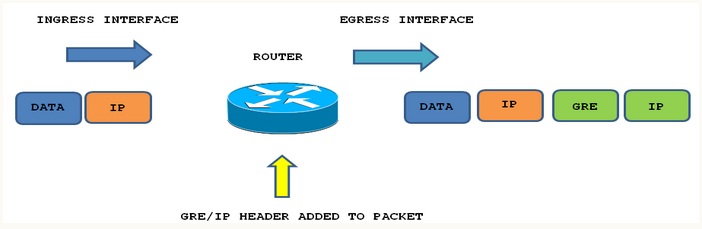
Configuring GRE Tunnel:
Configuring a GRE tunnel involves creating a tunnel interface, which is a logical interface. Then you must configure the tunnel endpoints for the tunnel interface.
To configure the tunnel source and destination, issue the tunnel source {ip-address | interface-type} and tunnel destination {host-name | ip-address} commands under the interface configuration mode for the tunnel.
The below example explain about how to create simple GRE tunnels between endpoints and the necessary steps to create and verify the GRE tunnel between the two networks.R1's and R2's Internal subnets(192.168.1.0/24 and 192.168.2.0/24) are communicating with each other using GRE tunnel over internet.Both Tunnel interfaces are part of the 172.16.1.0/24 network.

First step is to create our tunnel interface on R1 and R2 :
R1R2
R1(config)# interface Tunnel1 R1(config-if)# ip address 172.16.1.1 255.255.255.0 R1(config-if)# ip mtu 1400 R1(config-if)# ip tcp adjust-mss 1360 R1(config-if)# tunnel source 1.1.1.1 R1(config-if)# tunnel destination 2.2.2.2 | R2(config)# interface Tunnel1 R2(config-if)# ip address 172.16.1.2 255.255.255.0 R2(config-if)# ip mtu 1400 R2(config-if)# ip tcp adjust-mss 1360 R2(config-if)# tunnel source 2.2.2.2 R2(config-if)# tunnel destination 1.1.1.1 |
Since GRE is an encapsulating protocol, we adjust the maximum transfer unit (mtu) to 1400 bytes and maximum segment size (mss) to 1360 bytes. Because most transport MTUs are 1500 bytes and we have an added overhead because of GRE, we must reduce the MTU to account for the extra overhead. A setting of 1400 is a common practice and will ensure unnecessary packet fragmentation is kept to a minimum.
After configuring tunnel,two tunnel endpoints can see each other can verify using an icmp echo from one end.
R1# ping 172.16.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
Workstations on either network will still not be able to reach the other side unless a routing is configure on each router.Here We will configure static route on both router.
R1(config)# ip route 192.168.2.0 255.255.255.0 172.16.1.2
R2(config)# ip route 192.168.1.0 255.255.255.0 172.16.1.1
Now both networks (192.168.1.0/24 and 192.168.2.0/24) are able to freely communicate with each other over the GRE Tunnel .
Reference:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Here is a sample config for GRE.
GRE TUNNEL
Consider the following topology
Router1 [S0](64.45.15.17) ------ Internet -------(65.17.89.11)[S0]Router2---192.168.1.0/24
|_(10.0.0.1)_____________GRE Tunnel____________________(10.0.0.2)_|
Router1
*******
interface Tunnel0
ip address 10.0.0.1 255.255.255.252
tunnel source 64.45.15.17
tunnel destination 65.17.89.11
Router2
*******
interface Tunnel0
ip address 10.0.0.2 255.255.255.252
tunnel source 65.17.89.11
tunnel destination 64.45.15.17
And just apply the necessary routes for those tunnels:
for example
ip route 192.168.1.0 255.255.255.0 Tunnel0
About Keepalives here is the information:
Router1(config)#interface Tunnel1
Router1(config-if)#keepalive
By default, this keepalive command sends a packet through the tunnel to check its status
once every 10 seconds. If there is no response to three successive polls, the router
declares the tunnel interface to be down. So, this will change the tunnel's status about
30 seconds after a failure.
You can adjust both the time interval and the number of retries. For example, to send a
keepalive packet every five seconds, but to keep the default three retry limit, you could
use the following command:
Router1(config)#interface Tunnel1
Router1(config-if)#keepalive 5
If you want to change the number of retries, you can specify the new value after the time
interval. The following example will send a keepalive packet every three seconds, and will
declare the tunnel down if it doesn't hear a response back to two successive keepalive
tests:
Router1(config)#interface Tunnel1
Router1(config-if)#keepalive 3 2
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
good explanation thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Dear Sachin,
Thanks for your feedback
Regards,
Ashish Shirkar
(Community Manager-Network Infrastructure)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Ashish,
Good overview. Do you need to configure static routes or is dynamic routing (OSPF) sufficient for the tunnel to operate?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Carlos,
Yes,you can also use dynamic routing ,Only endpoint should be reachable i.e your source and destination IP. Dynamic routing and tunnels combination can be a dangerous.You need to be careful when using a dynamic routing protocol bcoz it cause a GRE tunnel to avoid the recursive routing error message, which brings down the tunnel. This happens because the routers need to have a good path through the network to carry the tunnel to its destination.Make sure that the routers never get confused and think that the best path to the tunnel destination is through the tunnel itself.you can refer this documents for the same
Regards,
Ashish Shirkar
Community Manager-NI
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
nice thanks for the config
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
nice one, simple and clear and easy to understand.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for this, but i want to ask, in your example, the internet ip addresses used, would one have to get them off an isp or one can just pick up any one?
tunnel source 64.45.15.17
tunnel destination 65.17.89.11
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For use on the Internet, you need addresses that are assigned by an ISP or the registry appropriate to your country (ARIN, RIPE, etc.).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have an issue with a new GRE tunnel:
I can ping the tunnel source and destination addresses and the tunnel seems to be up, but I can't ping the endpoints...
I checked all configs and compared them to another working tunnel, maybe someone has an idea? :-)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
check your routes
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
as long as both of them have the route of the addresses used in the tunnel source and destination.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Tom,
If you the tunnel is up and you are able to ping the tunnel source & destination ips then there is definetly an issue with the routing which is configured for the endpoints, you should check if the routes are configured rightly.
thanks, Veneet
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Thank you all for the possible answers. But it was another solution. Because of the tunnel vrf command I had left out. This would have worked if the used Loopback was part of the General/Generic/Unnamed vrf.
DCAT1S4-Edge#sh vrf
Name Default RD Protocols Interfaces
CustomerX 6:6 ipv4 Lo1541
CustomerX-Q1541 1541:1541 ipv4 Tu154128
Vl1541
interface Tunnel154128
description CustomerX-V1541-Registration
ip vrf forwarding CustomerX-Q1541
ip address 192.168.212.21 255.255.255.252
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source Loopback1541
tunnel destination 192.168.201.43
-> tunnel vrf CustomerX <-
Thanks!
Best regards, Tom
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you so much for the information and the explanation. It was so simple and straight forward. ![]()
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: