Introduction
Rogue Management, Attack Detection and Threat Mitigation
WLAN Security - Vulnerabilities and Threats

Cisco Rogue Management Diagram - Multiple Methods

Listening for Rogues - Two Different AP modes for RRM Scanning

RRM Channel Scanning
Local Mode AP

Monitor Mode AP

802.11n Rogue Detection

Rogue Classification Rules
Concept

Examples

Configuration

WCS Security Dashboard

Rogue Detector AP Mode
Concept

Example Deployment Scenario

Operation

Configuraiton

Rogue Location Discovery Protocol
Concept

Operation

Automatic Operation

Switchport tracing
Concept
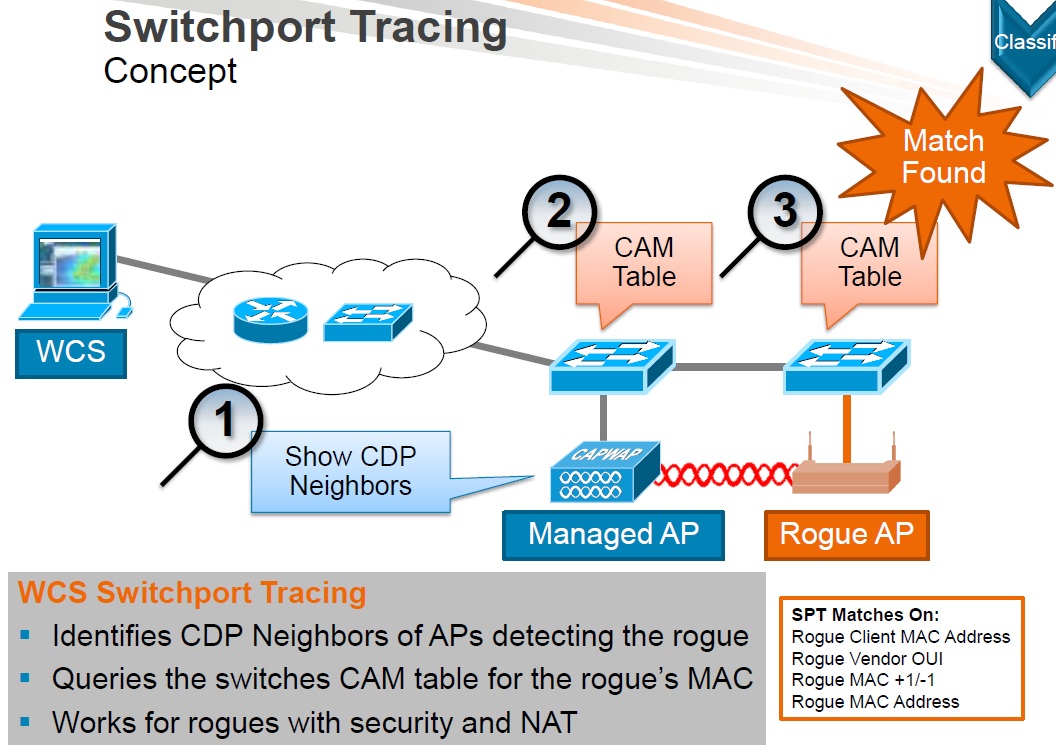
Operation (Cont.)

Rogue Location
On-Demand With WCS

In Real-Time with WCS and MSE Context-Aware

Rogue Containment
Concept

Local Mode AP's

Monitor Mode APs

Auto-Containment Configuration

More Information
Best Practices For Outdoor Wireless Security
Wireless Virtual LAN Deployment Guide