- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ACS 5.3 Configuring 802.1x
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACS 5.3 Configuring 802.1x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2012 04:59 PM - edited 03-10-2019 06:44 PM
Trying to configure 802.1x with ACS 5.3, have some general doubts about how to make it, this is what I got for the moment:
ACS 5.3 = 192.168.240.28
AD = 192.168.251.97
Switch = 192.168.240.171
IOS device config
Already configured and running Device Administration using Tacacs, mising with Radius aaa commands:
aaa group server tacacs+ TACACS_PLUS
server 192.168.240.28
!
aaa group server radius RADIUS_1x
server 192.168.240.28 auth-port 1812 acct-port 1813
!
aaa authentication login default group TACACS_PLUS
aaa authentication login no_tacacs enable local
aaa authentication enable default group RADIUS_1x
aaa authentication dot1x default group RADIUS_1x
aaa authorization config-commands
aaa authorization exec no_tacacs local
aaa authorization commands 15 TACACS_PLUS group tacacs+
aaa authorization network default group RADIUS_1x
aaa authorization auth-proxy default group RADIUS_1x
aaa accounting send stop-record authentication failure
aaa accounting update newinfo
aaa accounting dot1x default start-stop group RADIUS_1x
aaa accounting exec default start-stop group TACACS_PLUS
aaa accounting network default start-stop group TACACS_PLUS
aaa accounting connection default start-stop group TACACS_PLUS
aaa accounting system default start-stop group RADIUS_1x
!
tacacs-server host 192.168.240.28 port 49 key 7 104D0617040717180F05
tacacs-server directed-request
radius-server attribute 8 include-in-access-req
radius-server host 192.168.240.28 auth-port 1812 acct-port 1813
radius-server timeout 20
radius-server key 7 094F410718151201080D
radius-server vsa send authentication
!
dot1x system-auth-control
!
errdisable detect cause security-violation shutdown vlan
errdisable recovery cause security-violation
!
interface GigabitEthernet0/24
switchport mode access
switchport voice vlan 7
dot1x pae authenticator
dot1x port-control auto
dot1x host-mode multi-host
dot1x timeout quiet-period 15
spanning-tree portfast
spanning-tree bpduguard enable
ACS 5.3 Configuration until now






I have a document on how to configure this on ACS 4.2, but I have some problems trying to configure on ACS 5.3.
I'll appreciate a lot any ideas that could help me on this.
Regards,
Juan Carlos
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2012 05:10 PM
I try to test the conection to radius server, but I have a problem since here, this is the error message:
SW-LAB#test aaa group RADIUS_1x juancarlos.arias 12345 legacy
Attempting authentication test to server-group RADIUS_1x using radius
No authoritative response from any server.
I appreciate any ideas that could help.
Thanks,
Juan Carlos Arias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 09:33 AM
Hello Juan Carlos,
Is the ACS reporting any Failure under the reports for RADIUS Authentications?
Also, can you verify the Access Services Rules in order to confirm that the request is hitting the appropriate rule to get to "Network Access" Service rule?
If there are no hitcounts increasing for Authorization, Identity or even the Access Service Selection Rule then the ACS might be dropping the request before processing it. Have you already defined the IOS switch as a RADIUS AAA Client with the appropriate shared secret?
Enable "debug aaa authentication" and "debug radius" and perform the test command again. If you see timeouts we will have to collect a capture on the ACS switchport (SPAN Session) in order to verify that the traffic is getting to the ACS.
Feel free to share the debugs outputs with us.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 02:57 PM
Hello Carlos,
On ACS reporting I got this message errors:
24616 RADIUS token identity store received timeout error |
22059 The advanced option that is configured for process failure is used. |
22062 The 'Drop' advanced option is configured in case of a failed authentication request. |
On Access Services Rules, the request is hitting the correct rule, look at screenshot (Rule-2):

But, I got no hit counts on Authorization policy, I retype again the shared secret to be sure, but always timeout.
000143: Jan 19 16:39:23.421 GDL: RADIUS(00000000): Started 20 sec timeout
000144: Jan 19 16:39:40.836 GDL: RADIUS(00000000): Request timed out
000145: Jan 19 16:39:40.836 GDL: %RADIUS-4-RADIUS_DEAD: RADIUS server 192.168.240.28:1812,1813 is not responding.
000146: Jan 19 16:39:40.836 GDL: %RADIUS-4-RADIUS_ALIVE: RADIUS server 192.168.240.28:1812,1813 is being marked alive.
Maybe this policy is missing something:

Identity policy has hits matches:

This are the results when enabling debugs:
000150: Jan 19 16:45:23.237 GDL: AAA: parse name=
000151: Jan 19 16:45:23.237 GDL: AAA/MEMORY: create_user (0x376C7D8) user='juancarlos.arias' ruser='NULL' ds0=0 port='' rem_addr='NULL' authen_type=ASCII service=LOGIN priv=1 initial_task_id='0', vrf= (id=0)
000152: Jan 19 16:45:23.237 GDL: RADIUS: Pick NAS IP for u=0x376C7D8 tableid=0 cfg_addr=0.0.0.0
000153: Jan 19 16:45:23.237 GDL: RADIUS(00000000): Config NAS IPv6: ::
000154: Jan 19 16:45:23.237 GDL: RADIUS: ustruct sharecount=1
000155: Jan 19 16:45:23.237 GDL: Radius: radius_port_info() success=0 radius_nas_port=1
000156: Jan 19 16:45:23.237 GDL: RADIUS/ENCODE: Best Local IP-Address 192.168.240.171 for Radius-Server 192.168.240.28
000157: Jan 19 16:45:23.237 GDL: RADIUS(00000000): Send Access-Request to 192.168.240.28:1812 id 1645/6, len 68
000158: Jan 19 16:45:23.237 GDL: RADIUS: authenticator 30 E1 BC 4D 61 E0 72 C0 - 02 A1 E8 3E 88 91 DA D9
000159: Jan 19 16:45:23.237 GDL: RADIUS: NAS-IP-Address [4] 6 192.168.240.171
000160: Jan 19 16:45:23.237 GDL: RADIUS: NAS-Port-Type [61] 6 Async [0]
000161: Jan 19 16:45:23.237 GDL: RADIUS: User-Name [1] 18 "juancarlos.arias"
000162: Jan 19 16:45:23.237 GDL: RADIUS: User-Password [2] 18 *
000163: Jan 19 16:45:23.237 GDL: RADIUS(00000000): Sending a IPv4 Radius Packet
000164: Jan 19 16:45:23.237 GDL: RADIUS(00000000): Started 20 sec timeout
000165: Jan 19 16:45:40.350 GDL: RADIUS(00000000): Request timed out
000166: Jan 19 16:45:40.350 GDL: RADIUS: Retransmit to (192.168.240.28:1812,1813) for id 1645/6
000167: Jan 19 16:45:40.350 GDL: RADIUS(00000000): Started 20 sec timeout
000168: Jan 19 16:45:59.392 GDL: RADIUS(00000000): Request timed out
000169: Jan 19 16:45:59.392 GDL: RADIUS: Retransmit to (192.168.240.28:1812,1813) for id 1645/6
000170: Jan 19 16:45:59.392 GDL: RADIUS(00000000): Started 20 sec timeout
000171: Jan 19 16:46:17.235 GDL: RADIUS(00000000): Request timed out
000172: Jan 19 16:46:17.235 GDL: RADIUS: Retransmit to (192.168.240.28:1812,1813) for id 1645/6
000173: Jan 19 16:46:17.235 GDL: RADIUS(00000000): Started 20 sec timeout
000174: Jan 19 16:46:37.133 GDL: RADIUS(00000000): Request timed out
000175: Jan 19 16:46:37.133 GDL: RADIUS: No response from (192.168.240.28:1812,1813) for id 1645/6
000176: Jan 19 16:46:37.133 GDL: RADIUS: No response from server
000177: Jan 19 16:46:37.133 GDL: AAA/MEMORY: free_user (0x376C7D8) user='juancarlos.arias' ruser='NULL' port='' rem_addr='NULL' authen_type=ASCII service=LOGIN priv=1 vrf= (id=0)
Just as you said, there timeouts, I´ll proceed to collect packets on ACS port, please hold on some minutes.
Thanks again for your time.
Juan Carlos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 03:11 PM
Juan Carlos,
How is the Identity Store MNCH-Radius configured? Are you trying to authenticate against an OTP database like RSA?
The packet capture can wait until checking the Identity Store Sequence configuration.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 03:18 PM
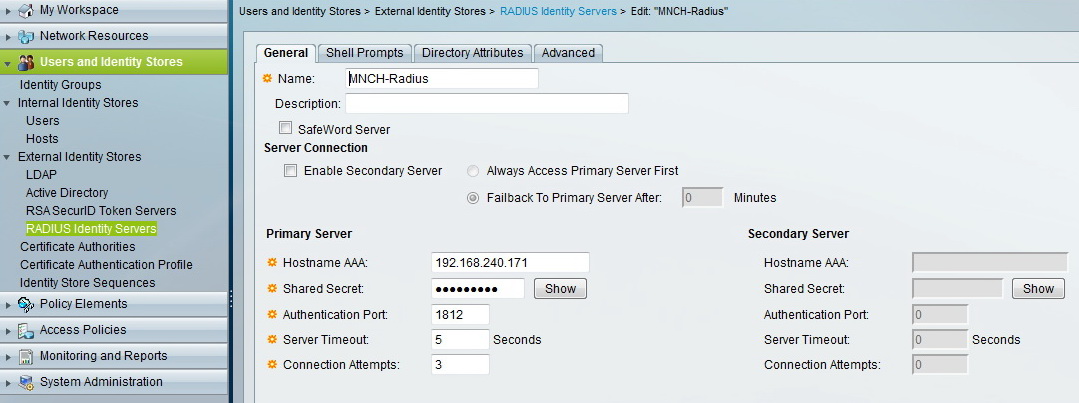
Carlos,
This is my Radius Identity Server configuration, don't know if this is the correct way to do it, maybe something there is missing, I want to authenticate with AD. IP Address of IOS device (NAS) = 192.168.240.171


Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 03:23 PM
Hello Juan Carlos,
So, 192.168.240.171 is a Domain Controller of your Active Directory domain? Or is it a RADIUS microsoft Server like MS IAS or MS NPS?
If it is a Domain Controller for your AD domain then we should try to bind the ACS to the AD domain instead of configuring as an external RADIUS Server.
I am attaching a configuration example on how to bind the ACS to the AD Domain and which are the requirements.
Please confirm the above statements.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 03:44 PM
Carlos,
No, 192.168.240.171 is my IOS device, a switch.
Just to notice, I already bind the ACS to AD domain, cause I'm using it for Device Admin:

.. and also changed the Network Access Identity to AD instead of Identity Store MNCH-Radius. But on Network Access Authorization the hits count still in 0, I'm confuse with this policy, don't know what is missing.
Regards,
Juan Carlos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 03:49 PM
Carlos, with this change, now I can see on Radius reports that Authentication succeeded, maybe just need to fix Network Access Authorization, don't you think??
Evaluating Identity Policy |
15004 Matched rule |
15013 Selected Identity Store - AD1 |
24430 Authenticating user against Active Directory |
24416 User's Groups retrieval from Active Directory succeeded |
24420 User's Attributes retrieval from Active Directory succeeded |
24402 User authentication against Active Directory succeeded |
22037 Authentication Passed |
Evaluating Authorization Policy |
15006 Matched Default Rule |
15016 Selected Authorization Profile - Permit Access |
22065 Max sessions policy passed |
22064 New accounting session created in Session cache |
11002 Returned RADIUS Access-Accept |
Regards,
Juan Carlos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 04:01 PM
Juan Carlos,
Can you share the whole report? The Authorization condition does reference to an AD Group (MNCH-GDL) and also to the Authentication Method (EAP-MSCHAPV2).
The Test Command for authentication on the IOS will always go as PAP. We will not match the above condition as we are not using EAP-MSCHAPV2.
You need to either remove the EAP-MSCHAPV2 Condition or test with a 802.1x Complian client configured for PEAP (EAP-MSCHAPV2).
Hope this helps.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 05:02 PM
Ok Carlos, I make it simple, just AD as condition and authorization profile, I tested with compliant client, and still receiving timeout, and Network Access Authorization still in 0, here is the debug:
001250: Jan 19 18:40:58.028 GDL: AAA/BIND(0000002F): Bind i/f
001251: Jan 19 18:40:58.237 GDL: %AUTHMGR-5-START: Starting 'dot1x' for client (f04d.a2a2.a028) on Interface Gi0/24 AuditSessionID C0A8F0AB0000001101B6C743
001252: Jan 19 18:41:00.007 GDL: %LINK-3-UPDOWN: Interface GigabitEthernet0/24, changed state to up
001253: Jan 19 18:41:01.014 GDL: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/24, changed state to up
001254: Jan 19 18:41:08.547 GDL: AAA/AUTHEN/8021X (0000002F): Pick method list 'default'
001255: Jan 19 18:41:08.547 GDL: RADIUS/ENCODE(0000002F):Orig. component type = Dot1X
001256: Jan 19 18:41:08.547 GDL: RADIUS(0000002F): Config NAS IP: 0.0.0.0
001257: Jan 19 18:41:08.547 GDL: RADIUS(0000002F): Config NAS IPv6: ::
001258: Jan 19 18:41:08.555 GDL: RADIUS/ENCODE(0000002F): acct_session_id: 37
001259: Jan 19 18:41:08.555 GDL: RADIUS(0000002F): sending
001260: Jan 19 18:41:08.555 GDL: RADIUS/ENCODE: Best Local IP-Address 192.168.240.171 for Radius-Server 192.168.240.28
001261: Jan 19 18:41:08.555 GDL: RADIUS(0000002F): Send Access-Request to 192.168.240.28:1812 id 1645/27, len 246
001262: Jan 19 18:41:08.555 GDL: RADIUS: authenticator 27 15 50 22 ED AB FC 34 - F1 24 56 87 30 6F 7D F9
001263: Jan 19 18:41:08.555 GDL: RADIUS: User-Name [1] 18 "juancarlos.arias"
001264: Jan 19 18:41:08.555 GDL: RADIUS: Service-Type [6] 6 Framed [2]
001265: Jan 19 18:41:08.555 GDL: RADIUS: Vendor, Cisco [26] 27
001266: Jan 19 18:41:08.555 GDL: RADIUS: Cisco AVpair [1] 21 "service-type=Framed"
001267: Jan 19 18:41:08.555 GDL: RADIUS: Framed-MTU [12] 6 1500
001268: Jan 19 18:41:08.555 GDL: RADIUS: Called-Station-Id [30] 19 "00-1C-0E-08-69-98"
001269: Jan 19 18:41:08.555 GDL: RADIUS: Calling-Station-Id [31] 19 "F0-4D-A2-A2-A0-28"
001270: Jan 19 18:41:08.555 GDL: RADIUS: EAP-Message [79] 23
001271: Jan 19 18:41:08.555 GDL: RADIUS: 02 01 00 15 01 6A 75 61 6E 63 61 72 6C 6F 73 2E 61 72 69 61 73 [ juancarlos.arias]
001272: Jan 19 18:41:08.555 GDL: RADIUS: Message-Authenticato[80] 18
001273: Jan 19 18:41:08.555 GDL: RADIUS: E5 92 90 F9 39 F2 EA A9 E4 B2 C9 02 12 9D EA B0 [ 9]
001274: Jan 19 18:41:08.555 GDL: RADIUS: EAP-Key-Name [102] 2 *
001275: Jan 19 18:41:08.555 GDL: RADIUS: Vendor, Cisco [26] 49
001276: Jan 19 18:41:08.555 GDL: RADIUS: Cisco AVpair [1] 43 "audit-session-id=C0A8F0AB0000001101B6C743"
001277: Jan 19 18:41:08.555 GDL: RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
001278: Jan 19 18:41:08.555 GDL: RADIUS: NAS-Port [5] 6 50024
001279: Jan 19 18:41:08.555 GDL: RADIUS: NAS-Port-Id [87] 21 "GigabitEthernet0/24"
001280: Jan 19 18:41:08.555 GDL: RADIUS: NAS-IP-Address [4] 6 192.168.240.171
001281: Jan 19 18:41:08.555 GDL: RADIUS(0000002F): Sending a IPv4 Radius Packet
001282: Jan 19 18:41:08.555 GDL: RADIUS(0000002F): Started 20 sec timeout
001283: Jan 19 18:41:26.507 GDL: RADIUS(0000002F): Request timed out
001284: Jan 19 18:41:26.507 GDL: RADIUS: Retransmit to (192.168.240.28:1812,1813) for id 1645/27
001285: Jan 19 18:41:26.507 GDL: RADIUS(0000002F): Started 20 sec timeout
Complete Report:









aaa group server tacacs+ TACACS_PLUS
server 192.168.240.28
!
aaa group server radius RADIUS_1x
server 192.168.240.28 auth-port 1812 acct-port 1813
!
aaa authentication login default group TACACS_PLUS
aaa authentication login no_tacacs enable local
aaa authentication enable default group RADIUS_1x
aaa authentication dot1x default group RADIUS_1x
aaa authorization config-commands
aaa authorization exec no_tacacs local
aaa authorization commands 15 TACACS_PLUS group tacacs+
aaa authorization network default group RADIUS_1x
aaa authorization auth-proxy default group RADIUS_1x
aaa accounting send stop-record authentication failure
aaa accounting update newinfo
aaa accounting dot1x default start-stop group RADIUS_1x
aaa accounting exec default start-stop group TACACS_PLUS
aaa accounting network default start-stop group TACACS_PLUS
aaa accounting connection default start-stop group TACACS_PLUS
aaa accounting system default start-stop group RADIUS_1x
!
dot1x system-auth-control
!
interface GigabitEthernet0/24
switchport mode access
switchport voice vlan 7
authentication port-control auto
authentication violation protect
dot1x pae authenticator
dot1x timeout quiet-period 15
spanning-tree portfast
spanning-tree bpduguard enable
!
tacacs-server host 192.168.240.28 key 7 104D0617040717180F05
tacacs-server directed-request
radius-server attribute 8 include-in-access-req
radius-server host 192.168.240.28 auth-port 1812 acct-port 1813 key 7 15110402053A2E372B32
radius-server timeout 20
radius-server key 7 0110090A5A1B031C224D
radius-server vsa send authentication
The compliant client should have access to Vlan 60.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 05:05 PM
Juan Carlos,
Is the ACS still reporting an Authentication Success? We need the report for the authentication attempt.
Please share it with us as well. Configuration seems to be fine now. On the report we should be able to see the AD Group MNCH-GDL as an attribute for the user under "Other Attributes" in order for us to match the authorization rule.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 05:09 PM
Carlos, sorry I missed that, here it is using compliant client:
RADIUS Status:
EAP session timed out :
Radius authentication failed for USER: juancarlos.arias MAC: F0-4D-A2-A2-A0-28 AUTHTYPE: Radius authentication failed.
But if I use test command:
On Radius report Authentication succeeded, but not on IOS
SW-LAB#test aaa group RADIUS juancarlos.arias 12345 new-code
User rejected
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 05:18 PM
Juan Carlos,
EAP Session Timeout can be a tricky one as it has always been related to Supplicant issues. It is hard to prove but on TAC we always download and install Cisco Secure Services Client (CSSC - Cisco Supplicant).
You can download the Supplicant CSSC version 4.x and install it on your XP Machine (Does not support Vista/7). You need a valid Cisco CCOiD to download it:
Products > Wireless > Client Adapters and Client Software > Cisco Secure Services Client > Secure Services Client Software > Windows XP-4.2.3
You migth want to test with it or open a TAC case for an engineer to deeper troubleshoot the issue.
The EAP Session Timeout is usually related to a Challenge send by the ACS that the supplicant is not able to Respond.
If you try with a different client (Let's say Windows XP Client with Windows Native supplicant) does it work? If not, we will have to try the CSSC supplicant installed on a XP machine.
If needed I can shared configuration screenshots for the CSSC but can take me sometime.
If this has been helpful please rate.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2012 05:54 PM
Carlos,
I´m recreating a lab for a customer that all machines are W7, so CSSC is not useful. So all this, it's because ACS v5.3?? Last year I recreate a lab using ACS v4.2 and had no problem with XP and W7, do I have to move to that version?? I read some comments that ACS 5.1 it's better than 5.3, what do you recommend??
It will be helpful if you add screenshots for CSSC.
Regards,
Juan Carlos
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: