- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Dual Machine Certs - ISE 2.1
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Dual Machine Certs - ISE 2.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 11:26 AM - edited 02-21-2020 10:36 AM
Hello,
Our organization is looking to move from an existing CA which is pushing to computer certs to a new CA. Since ISE can only trust one CA at a time, we want to push out new certs to all the machines from the new CA for several days and then make the trusted root switch on ISE.
The problem we are running into is, once the workstations get the additional CA cert the clients immediately begin to fail authentication to ISE for untrusted root. It is wanting to use the new cert rather than the existing.
Does anyone have a solution to this issue with dual client certs on a windows machine? Is there a way from either ISE side or from Windows side to force the client to use the older cert until we are ready to make the switch?
- Labels:
-
Other NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 04:36 PM
I assume you are talking about certs for the EAP role?
Have you considered issuing the new client certs with a "Not Before" date that is on a day when you plan to change the ISE server cert? That might be one approach. Not sure how the various OS's would handle that situation though (i.e. how to prevent the OS from using that new cert until you are ready)
You can certainly install the new CA certificate chain into all of your PSN's as Truested Certs - that won't have any effect.
Importing a new EAP cert into ISE will take the PSN down for 10-15 minutes in my experience.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2017 07:48 AM
The new root and sub certs will be in imported into the Trusted Certs, which can be done ahead of time. But when I import the certificate chain into the PSN's, I have to select it's usage to authenticate with Admin nodes and EAP. I was told you cannot have two certificates using Admin and EAP on the PSN. Is there a way to have it accept certs from both CA's for authentication?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 06:24 AM
For EAP-TLS with certificates, both client and server needs to validate each others certificate. And AFAIK, this each validation is independent of each other. So if you added the new CA certificate into the trusted root store, the client cert will be validated if it uses the old or new CA hierarchy.
For server side validation, there is a setting inside the supplicant (Windows native or Anyconnect) to chose which Ca to trust. I believe you can check multiple CA's in this option. So you can first check both old and new CA certs on the client and then change the ISE EAP cert.
When I last made the change for EAP certificate, I did not see a downtime. Only when the Admin certificate was changed, did it restart the services.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2017 08:36 AM - edited 10-18-2017 08:37 AM
Starting Windows 8/Server 2012 you can do certificate filtering in the GPO that configures the authentication policies, it gives you more control over the certificate selection process. You should be able to force client to select the old cert that way. Something similar might be possible with Windows 7 native supplicant, haven't looked at this much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 08:54 AM
Thanks all for your replies,
If I can control which one is sent/primary through GPO that would be a great solution. I spent some time digging and could not find any options around this though.
@agrissimanis do you know the location of this GPO setting? All we set internally is enabling auto-enroll and letting the permissions on the certificates determine which ones get auto-deployed.
Thanks!
Cody
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 01:03 AM
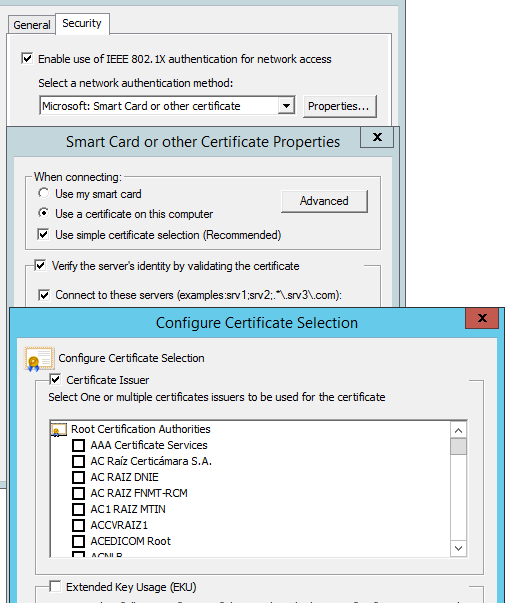
Check Computer Configuration -> Policies -> Windows Settings -> Wired/Wireless IEEE 802.3 policies. I guess you have entry there to configure your corporate clients. When you go into Properties -> Security -> Smart Card or other certificate -> Properties. There is a new "Advanced" button available, that is where you can configure some additional certificate selection options.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide