- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE AD Sites and Services
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE AD Sites and Services
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2018 12:09 PM - edited 02-21-2020 10:46 AM
Have a 6 node deployment; 3 nodes in DC1 and 3 nodes in DC2. PAN primary is in DC1 and MnT is in DC2. 2 PSN per DC.
Wireless controllers are centralized at the DCs and therefore, the wireless client VLANs are local to the DC.
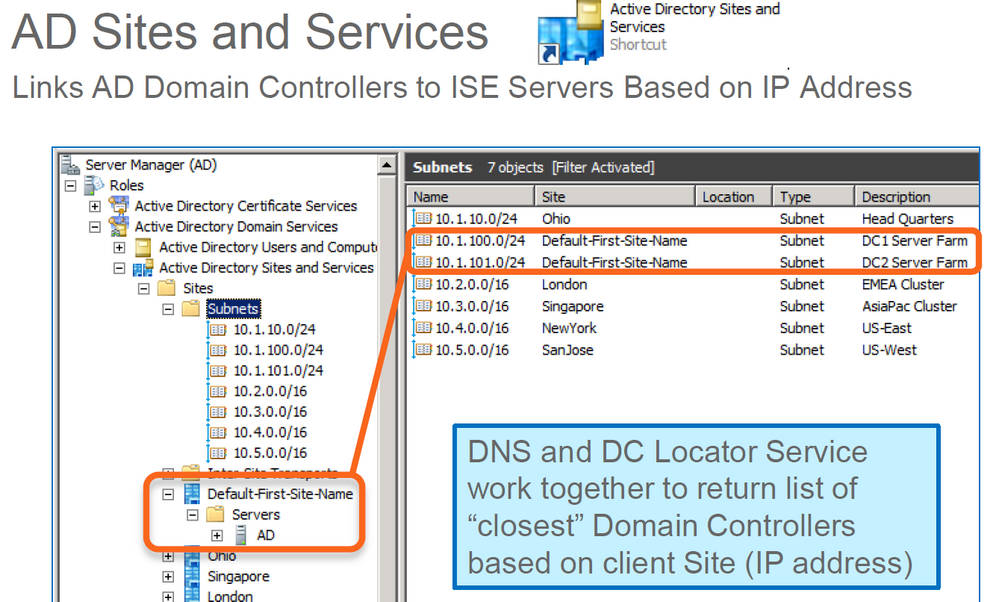
We use AD sites and services. The wireless subnets were input into sites and services based on the site they wireless client are located, ie a DC local to the site (not a DC at the data center).
I need to determine if ISE is sending the re/authentication back to the local DC (based on AD sites and services pointing the subnet to the site domain controllers) or if ISE is using the domain controller local to the data center.
- Labels:
-
Other NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2018 03:23 AM - edited 02-22-2018 03:24 AM
Hi,
I don't see the connection between WIFI clients/AD Sites & Services + ISE.
If you want ISE to authenticate clients using a specific DC, ISE's subnet should be included in the same site as the DC you want to use. My thought is that the DC you're seeing in ISE AD join point is the DC you're now using.
Thanks,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2018 12:32 PM
Hello Octavian,
i have the similar problem with some remote location with its local DC & PSN getting to central DC for authentication. In the ISE PAN i have configuration of specific FQDN (auth-ldpa.local) in Administration>External Identity Sources>LDAP>CUSTOMERSPECIFIC_AD_LDAP > LDAP Identity Source>Connection tab , which resolves into central DC from everywhere except of remote PSN where i configured "ip host <IP-of-the-site-local-DC> auth-ldap.local"to force remote PSN to go to its local DC. but it doesnt work and remote PSN explicitly shows central DC in its record in Administration>Active Directory>CUSTOMER-AD>Connection. As i understood your message, to overcome this the AD must be reconfigured with adding remote site and moving there both remote DC and remote location subnets. Is it correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 01:52 AM
Hi,
I think you should open a new post, but to answer your question, I think you mixed the AD part with the LDAP source sequence.
Use only one of them if you're referring to the same target. Why use both for the same AD setup? If your infrastructure uses AD, use the AD identity source. If you're using something else besides MS AD, use LDAP.
The static mapping should be used for some other scenarios (gues with different physical port on PSN).
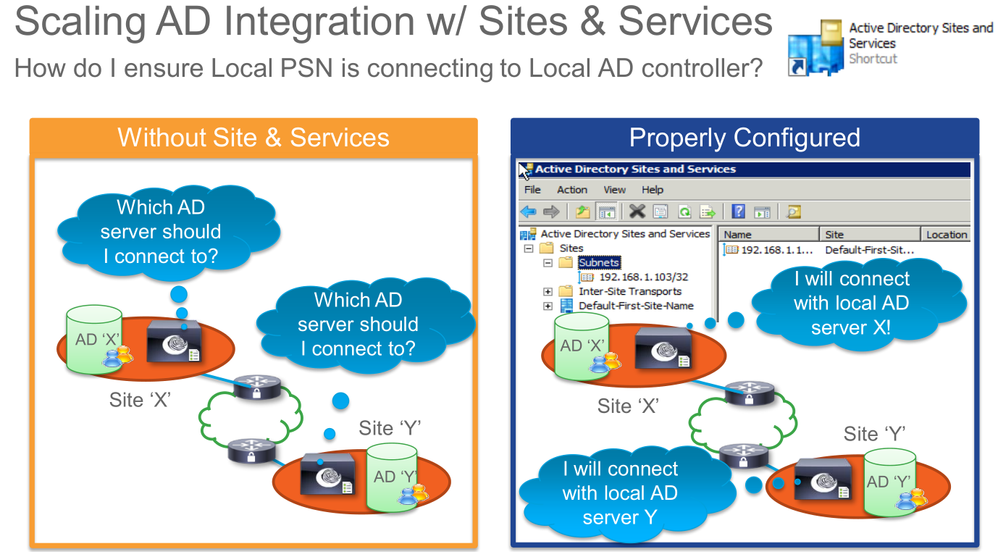
For the local PSN to use the local DC, the sysadmin guys have to configure AD Sites and Services and to make sure that the subnet(s) for both the PSN and the local DC belong to the same 'Site'.
Check BRKSEC-3699 (CiscoLive) and there is another but I don't remember the number which talked exclusively about the AD Connector in ISE.
Thanks,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 02:02 AM
Hello Octavian
Many thanks for the feedback. I’ve managed to find proper BRKSEC & it states about the same u’ve just mentioned.
This document claims hard-coding of the DC’s IP in PSN as being a bad practice, but says nothing about how it can be implemented.
Do you have any hints on it?
Br, Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 02:06 AM - edited 02-23-2018 02:06 AM
Hi Andy,
Unfortunately, this is all I have as an MS link:
An M$ guy would know for sure :)
Thanks,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 02:10 AM
But i've been asking for the configuring PSN node itself to connect to the custom DC. U might miss sence of my Q
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 05:52 AM
Hi Andy,
Sorry, I was carried away. To be honest, I'm not sure how you could do that. (and I would not do it if I were you; just use sites and services)
Maybe this can be of help:
https://communities.cisco.com/thread/84704?start=0&tstart=0
Thanks,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 05:10 AM
Hi Octavian
Thank for the reference. now i'm absolutely sure that hardcoding of DC to use on PSN is done via Active Directory Advanced Tuning. But one (perhaps Cisco TAC) need to know the variable (perhaps one under REGISTRY) to implement this :)
Cheers
@Octavian Szolga wrote:
Hi Andy,
Sorry, I was carried away. To be honest, I'm not sure how you could do that. (and I would not do it if I were you; just use sites and services)
Maybe this can be of help:
https://communities.cisco.com/thread/84704?start=0&tstart=0
Thanks,
Octavian
@Octavian Szolga wrote:
Hi Andy,
Sorry, I was carried away. To be honest, I'm not sure how you could do that. (and I would not do it if I were you; just use sites and services)
Maybe this can be of help:
https://communities.cisco.com/thread/84704?start=0&tstart=0
Thanks,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2022 01:04 AM
Hey Andi,
could you metion the proper BRKSEC number please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2022 01:40 PM
I believe he was referring to BRKSEC-2132 -- What's new in ISE Active Directory Connector. This session was from 2016, so it is no longer available on the CiscoLive site.
If you do a search, however, you should be able to find a copy hosted elsewhere.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2022 11:35 PM
i think it was BRKSEC-3697 Advanced ISE Services, Tips & Tricks
but try also to use reference Gregg gave.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 06:02 AM
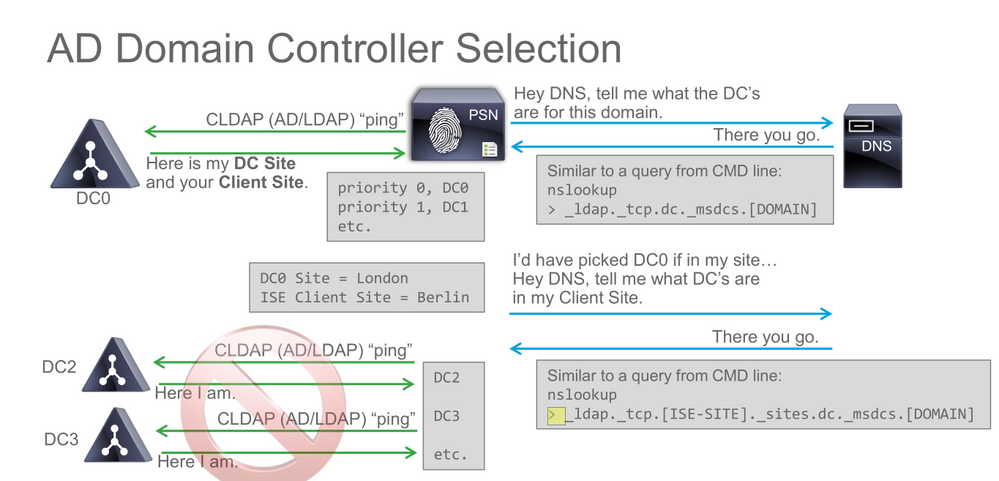
Octavian, thanks for the response. So ISE will use whatever domain controller is shown under Administration > External Identity Sources > Active Director. Sites and services has no bearing on the process.
As far as the wireless clients "sites and services" subnets are concerned (maybe need a new thread in mobility section), since their gateways and WLCs are physically located in the data center, does it make sense to point all wireless subnets in sites and services to the domain controllers at the data centers, instead of a domain controller locally at the site? From a traffic forwarding perspective, just want to confirm it wouldn't make sense for a client to be connected to a wifi network with the gateway in the data center, forward traffic back to the domain controller, back to the data center, and then back to the client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 07:11 AM
Hi,
Sites an services functionality is related to whatever you see in ISE AD section. You have to make sure that both PSN and DC belong to the same MS site.
Regarding the WIFI clients and your APs in local mode - all traffic sent to main DC/WLC - it makes sense to configure the clients subnet to be part of the same site as the DC server, because as you said, both networks are present in the DC, not locally in the branch. So make sure that sites and services is configured correct and that your clients are using the DC DNS servers so that your traffic won't bounce back and forth from DC to branch and so on.
Thanks,
Octavian
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide