- Cisco Community
- Technology and Support
- Online Tools and Resources
- Cisco Bug Discussions
- Re: CSCvf47808%20-%20Key%20Reinstallation%20attacks%20against%20WPA%20protocol%20-%2010
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 06:27 AM - edited 03-20-2019 09:38 PM
I have some AIR-CAP3702I-A-K9 APs controlled by a 2500 series WLC running 7.6.120.0.
Am I affected by this vulnerability. If yes , what is the fix release?
Solved! Go to Solution.
- Labels:
-
Cisco Bugs
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 09:40 AM
Aaron
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 09:40 AM
Aaron
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2017 03:52 AM
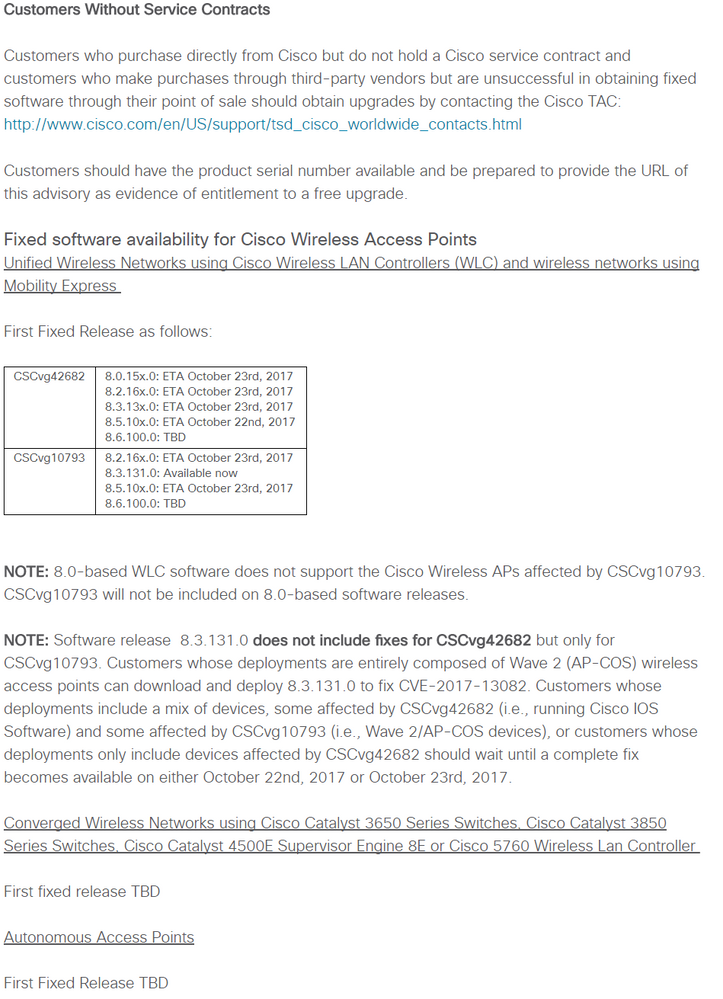
Cisco TAC has recommended anyone to HOLD OFF upgrading to 8.3.132.0. TAC has identified a Severity 1 bug which causes the controller to crash after upgrading to 8.3.132.0.
There are no reported issues in regards to other versions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 04:33 PM
Just a reminder that this vulnerability affects anything with a wireless NIC. It's not just wireless AP but also wireless clients as well. Patching the client will fix 9 out of 10 vulnerabilities but not CVE-2017-13082. (CVE-2017-13082 will be patched on the AP side.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 01:15 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide