- Cisco Community
- Technology and Support
- Online Tools and Resources
- Cisco Bug Discussions
- CSCvg10793%20-%20Key%20Reinstallation%20attacks%20against%20WPA%20protocol%20-%201
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2017 02:54 PM - edited 03-20-2019 09:37 PM
Hi,
Couple of weeks ago we have Installed some new AP2800i is our organization network and we did upgrade WLC 5508 software from 8.2.151 to 8.3.122 in which Cisco recommended.
Do I need to upgrade software again???
Please find information about new WAPs 2802i installed in attachment. If you need more information please don't hesitate to contact me.
I look forward to hearing from you soon.
Regards,
Daniel
Solved! Go to Solution.
- Labels:
-
Cisco Bugs
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 12:19 AM
@aghm wrote:
Do I need to upgrade software again???
Hi Daniel,
This vulnerability affects anything with a wireless NIC. It's not just wireless AP but also wireless clients as well. Patching the client will fix 9 out of 10 vulnerabilities but not CVE-2017-13082.
Perspective About the Recent WPA Vulnerabilities (KRACK Attacks)
There is no "workaround" for this vulnerability. Upgrade is the only way. It is your call to make the decision to upgrade or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 12:19 AM
@aghm wrote:
Do I need to upgrade software again???
Hi Daniel,
This vulnerability affects anything with a wireless NIC. It's not just wireless AP but also wireless clients as well. Patching the client will fix 9 out of 10 vulnerabilities but not CVE-2017-13082.
Perspective About the Recent WPA Vulnerabilities (KRACK Attacks)
There is no "workaround" for this vulnerability. Upgrade is the only way. It is your call to make the decision to upgrade or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 02:50 PM
Daniel,
The short answer is yes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 03:49 PM - edited 10-20-2017 04:23 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 03:49 PM - edited 10-20-2017 04:24 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 12:42 AM - edited 10-20-2017 12:43 AM
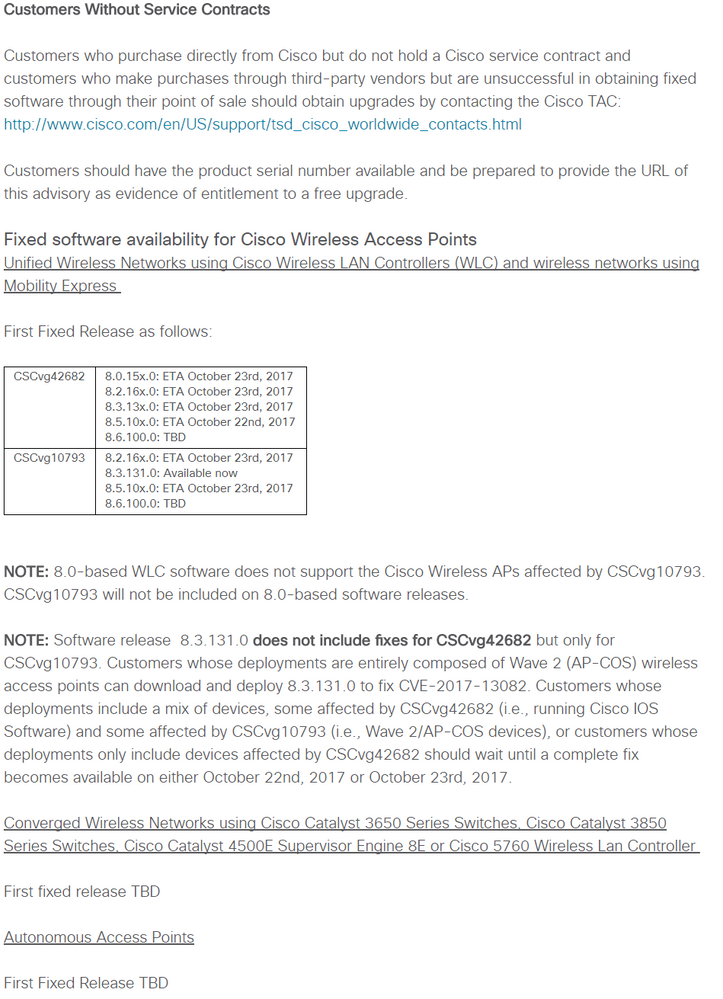
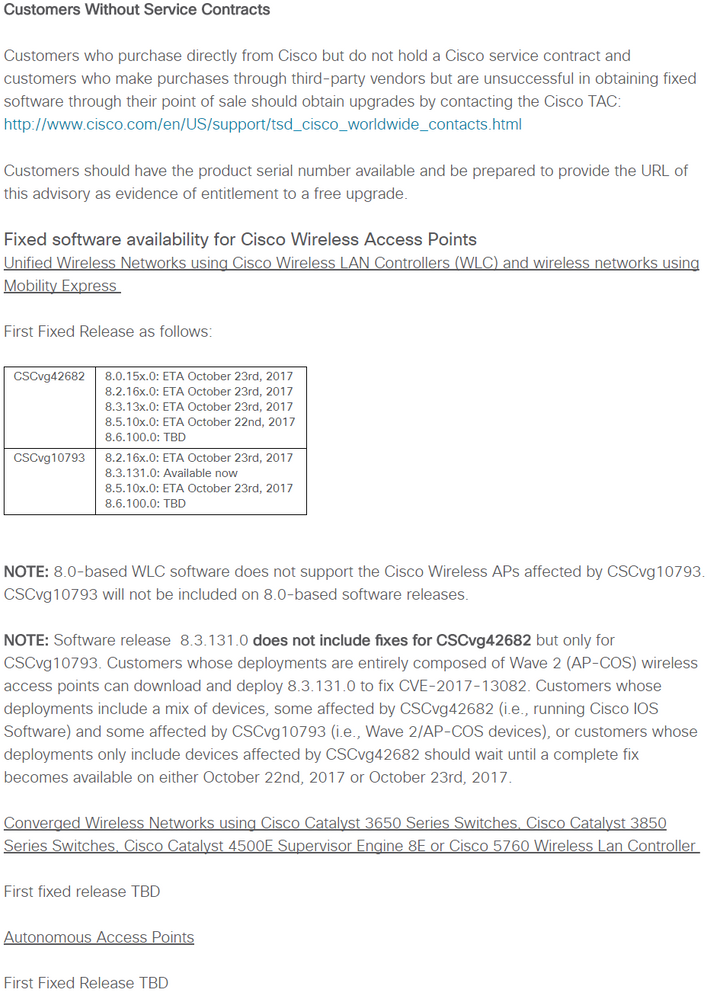
Latest update in BUD ID: CSCvf47808 and CSCvg10793, does not show 8.3.122.0 in affected release list. So wondering if 8.3.122.0 is affected.
Affected Releases
Support for FT was added in 7.2, all releases after that are affected if FT is enabled
Releases 7.0 and lower are not affected
8.5.103.0
8.4 all releases
8.3.100.0 to 8.3.121.0 for all AP types
8.3.130.0 Partially, fixed for IOS, affected for AP-COS
8.2 up to 8.2.160.0
8.1 all releases
8.0 up to 8.0.150.0
7.2 to 7.6 all releases
Resolved Releases
8.3.131.0 and higher
8.3.130.6 (escalation)
(additional releases will be included here as they are made available)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 01:02 AM - edited 10-20-2017 04:22 PM
8.3 is affected by CSCvf47808.
8.3.131.0 was released about 16 hours ago. In the Release Notes, under Resolved Caveats, CSCvf47808 is listed.
Please see updated post below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 04:22 PM
Kindly delay with doing any upgrade to 8.3.130.0. During their testing phase (after the release) they found some issues affecting non-Wave 2 APs. They've found what the issue is and they're testing the new fix before releasing the fix version on 23 October 2017.
I have updated my earlier post of the ETA of the fix to reflect the new development.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 01:15 AM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: