- Cisco Community
- Technology and Support
- Online Tools and Resources
- Cisco Bug Discussions
- Re: WLC 5520 KRACK Attack WPA2 Vulnerability (Fast Transition configured)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 09:16 AM - edited 03-20-2019 09:37 PM
We have some SSID's broadcast using WPA2 authentication and have "Fast Transition" configured.
Recently KRACK Attack vulnerability is released. does this security vulnerability have patch already?
TIA
Solved! Go to Solution.
- Labels:
-
Cisco Bugs
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 01:12 AM
Software fix for the KRACK vulnerability is now available for download. They are 8.0.152.0, 8.2.164.0, 8.3.132.0 and 8.5.105.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 02:04 PM - edited 10-17-2017 02:04 PM
Cisco will be releasing a fix very soon.
Remember that this vulnerability affects not just the APs but any wireless client with a wireless NIC. So patching the APs won't fix the issue as the wireless client(s) needs to be patched as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 06:59 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 11:16 PM
See here for more information: https://supportforums.cisco.com/t5/security-and-network-management/severe-flaw-in-wpa2-protocol-krack-attack/td-p/3199201
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 11:00 PM
Hi Mate,
If you have a WLAN with FT(802.11r) enabled, please follow the work around provided in this Cisco security advisory: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171016-wpa#workarounds, Please subscribe to notifications of this document for the latest news and fixes.
Disabling FT (802.11r) on the AP/WLC side is an effective workaround to the AP side vulnerability, and the client-side vulnerabilities will need to be addressed on the client side.
Regards,
Divya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2017 12:37 AM
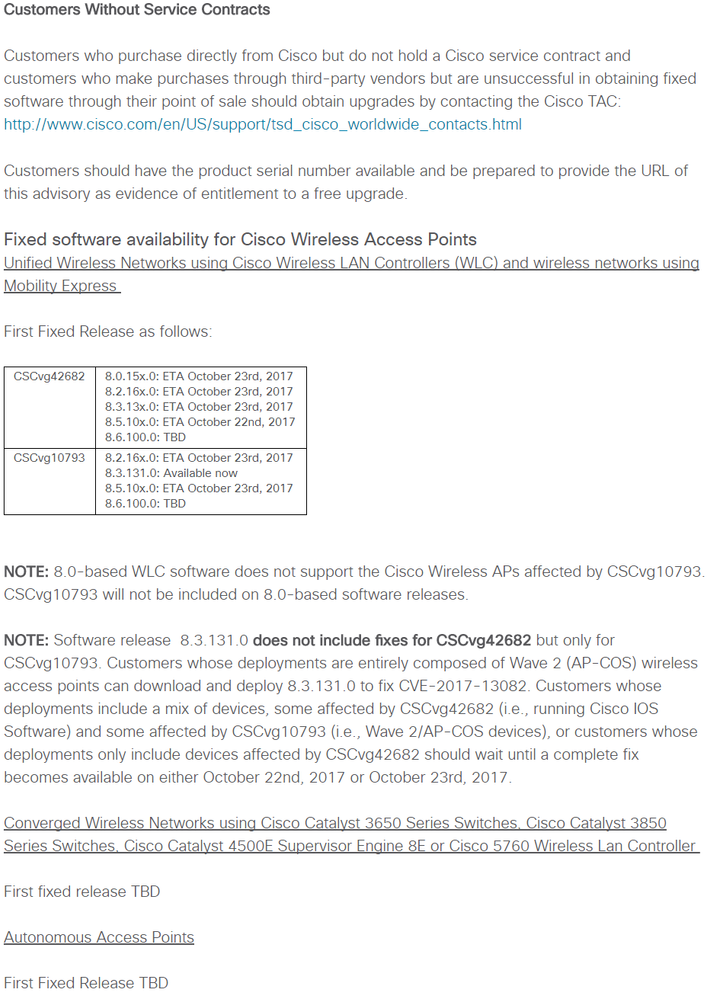
Here is schedule of software fix release dates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2017 04:54 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 01:12 AM
Software fix for the KRACK vulnerability is now available for download. They are 8.0.152.0, 8.2.164.0, 8.3.132.0 and 8.5.105.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2017 09:39 AM
Steve Saeger
Director, Network/Telecom
Mercy
3637 S. Geyer Rd.
St. Louis, MO 63127
Office: 314-364-3240 | Email: steven.saeger@mercy.net
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2017 10:05 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2017 03:46 AM
A quick update to anyone reading this thread and intending to upgrade to 8.3.132.0:
Cisco TAC has recommended anyone to HOLD OFF upgrading to 8.3.132.0. TAC has identified a Severity 1 bug which causes the controller to crash after upgrading to 8.3.132.0.
There are no reported issues in regards to other versions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2017 07:23 AM
Thanks for the heads-up, we'll postpone our scheduled upgrade then and wait for the stable update.
-
Cheers,
Mon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2017 07:27 AM
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171101-aironet1
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171101-aironet2
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171101-wlc1
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171101-wlc2
All those new issues are fixed in the following releases:
Prior to 8.0 Not vulnerable
8.0.152.0
8.2.164.0
8.2.164.0
8.3.132.0
8.4.100.0
8.5.110.0 (future release)
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: