- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cisco ASAv - HTTPS/ASDM not working -SSL lib error
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco ASAv - HTTPS/ASDM not working -SSL lib error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2017 03:16 AM - edited 02-21-2020 06:39 AM
I've downloaded the latest version of Cisco ASAv to carry out some evaluation in our VMware ESXi lab. I've installed the appliance and configured the management interface via CLI, but I can't seem to get it to accept a HTTPS/ASDM connection. It's failing on SSL handshake despite the having matching ciphers on both the client and ASAv. I'm getting the error:
SSL lib error. Function: ssl3_get_client_hello Reason: no shared cipher
However, if you look at the logs, there are indeed matching ciphers. Am I wrong in assuming that you can use the ASAv in a lab environment, with limited functionality, for evaluation purposes, without a licence? Surely ASDM should work?
Below is the Show Version followed by the logs which show that ciphers match, but I still get the SSL lib error.
ciscoasa# sh ver
Cisco Adaptive Security Appliance Software Version 9.8(2)
Firepower Extensible Operating System Version 2.2(2.52)
Device Manager Version 7.8(2)
Compiled on Sun 27-Aug-17 13:09 PDT by builders
System image file is "boot:/asa982-smp-k8.bin"
Config file at boot was "startup-config"
ciscoasa up 5 days 19 hours
Hardware: ASAv, 1024 MB RAM, CPU Pentium II 2933 MHz,
Model Id: ASAv5
Internal ATA Compact Flash, 1024MB
Slot 1: ATA Compact Flash, 8192MB
BIOS Flash Firmware Hub @ 0x0, 0KB
0: Ext: Management0/0 : address is 0050.5680.0693, irq 10
1: Ext: GigabitEthernet0/0 : address is 0050.5680.a342, irq 5
2: Ext: GigabitEthernet0/1 : address is 0050.5680.2086, irq 9
3: Ext: GigabitEthernet0/2 : address is 0050.5680.0c51, irq 11
4: Ext: GigabitEthernet0/3 : address is 0050.5680.7b8e, irq 10
5: Ext: GigabitEthernet0/4 : address is 0050.5680.66e1, irq 5
6: Ext: GigabitEthernet0/5 : address is 0050.5680.58d5, irq 9
7: Ext: GigabitEthernet0/6 : address is 0050.5680.e822, irq 11
8: Ext: GigabitEthernet0/7 : address is 0050.5680.3e0c, irq 10
9: Ext: GigabitEthernet0/8 : address is 0050.5680.0882, irq 5
License mode: Smart Licensing
ASAv Platform License State: Unlicensed
No active entitlement: no feature tier and no throughput level configured
*Memory resource allocation is more than the permitted limit.
Licensed features for this platform:
Maximum VLANs : 25
Inside Hosts : Unlimited
Failover : Active/Standby
Encryption-DES : Enabled
Encryption-3DES-AES : Enabled
Security Contexts : 0
Carrier : Disabled
AnyConnect Premium Peers : 2
AnyConnect Essentials : Disabled
Other VPN Peers : 50
Total VPN Peers : 50
AnyConnect for Mobile : Disabled
AnyConnect for Cisco VPN Phone : Disabled
Advanced Endpoint Assessment : Disabled
Shared License : Disabled
Total TLS Proxy Sessions : 2
Botnet Traffic Filter : Enabled
Cluster : Disabled
Serial Number: 9AT64WC9QLR
Image type : Release
Key version : A
Configuration last modified by enable_15 at 16:26:25.788 UTC Thu Nov 2 2017
ciscoasa#
%ASA-6-302013: Built inbound TCP connection 305 for Management:10.222.5.8/29031 (10.222.5.8/29031) to identity:10.73.40.22/443 (10.73.40.22/443)
%ASA-6-725001: Starting SSL handshake with client Management:10.222.5.8/29031 to 10.73.40.22/443 for TLS session
%ASA-7-725010: Device supports the following 21 cipher(s)
%ASA-7-725011: Cipher[1] : ECDHE-ECDSA-AES256-GCM-SHA384
%ASA-7-725011: Cipher[2] : ECDHE-RSA-AES256-GCM-SHA384
%ASA-7-725011: Cipher[3] : DHE-RSA-AES256-GCM-SHA384
%ASA-7-725011: Cipher[4] : AES256-GCM-SHA384
%ASA-7-725011: Cipher[5] : ECDHE-ECDSA-AES256-SHA384
%ASA-7-725011: Cipher[6] : ECDHE-RSA-AES256-SHA384
%ASA-7-725011: Cipher[7] : DHE-RSA-AES256-SHA256
%ASA-7-725011: Cipher[8] : AES256-SHA256
%ASA-7-725011: Cipher[9] : ECDHE-ECDSA-AES128-GCM-SHA256
%ASA-7-725011: Cipher[10] : ECDHE-RSA-AES128-GCM-SHA256
%ASA-7-725011: Cipher[11] : DHE-RSA-AES128-GCM-SHA256
%ASA-7-725011: Cipher[12] : AES128-GCM-SHA256
%ASA-7-725011: Cipher[13] : ECDHE-ECDSA-AES128-SHA256
%ASA-7-725011: Cipher[14] : ECDHE-RSA-AES128-SHA256
%ASA-7-725011: Cipher[15] : DHE-RSA-AES128-SHA256
%ASA-7-725011: Cipher[16] : AES128-SHA256
%ASA-7-725011: Cipher[17] : DHE-RSA-AES256-SHA
%ASA-7-725011: Cipher[18] : AES256-SHA
%ASA-7-725011: Cipher[19] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[20] : AES128-SHA
%ASA-7-725011: Cipher[21] : DES-CBC3-SHA
%ASA-7-725008: SSL client Management:10.222.5.8/29031 to 10.73.40.22/443 proposes the following 20 cipher(s)
%ASA-7-725011: Cipher[1] : ECDHE-ECDSA-AES128-SHA256
%ASA-7-725011: Cipher[2] : ECDHE-RSA-AES128-SHA256
%ASA-7-725011: Cipher[3] : AES128-SHA256
%ASA-7-725011: Cipher[4] : DHE-RSA-AES128-SHA256
%ASA-7-725011: Cipher[5] : DHE-DSS-AES128-SHA256
%ASA-7-725011: Cipher[6] : ECDHE-ECDSA-AES128-SHA
%ASA-7-725011: Cipher[7] : ECDHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[8] : AES128-SHA
%ASA-7-725011: Cipher[9] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[10] : DHE-DSS-AES128-SHA
%ASA-7-725011: Cipher[11] : ECDHE-ECDSA-AES128-GCM-SHA256
%ASA-7-725011: Cipher[12] : ECDHE-RSA-AES128-GCM-SHA256
%ASA-7-725011: Cipher[13] : AES128-GCM-SHA256
%ASA-7-725011: Cipher[14] : DHE-RSA-AES128-GCM-SHA256
%ASA-7-725011: Cipher[15] : DHE-DSS-AES128-GCM-SHA256
%ASA-7-725011: Cipher[16] : ECDHE-ECDSA-DES-CBC3-SHA
%ASA-7-725011: Cipher[17] : ECDHE-RSA-DES-CBC3-SHA
%ASA-7-725011: Cipher[18] : DES-CBC3-SHA
%ASA-7-725011: Cipher[19] : EDH-RSA-DES-CBC3-SHA
%ASA-7-725011: Cipher[20] : EDH-DSS-DES-CBC3-SHA
%ASA-7-725014: SSL lib error. Function: ssl3_get_client_hello Reason: no shared cipher
%ASA-6-302014: Teardown TCP connection 305 for Management:10.222.5.8/29031 to identity:10.73.40.22/443 duration 0:00:00 bytes 7 TCP FINs
Network routing is correct and a correct RSA SSL certificate has been generated.
Any help appreciated. Thanks.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2017 11:25 AM
juanmh8419@gmail.com
Skype: juanmh8419@hotmail.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 01:41 AM
Hi,
I've already run through all of the proposed solutions on that link and none of them work.
I always get the SSL Lib error, despite there being matching ciphers.
Dom.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2017 05:09 AM
It does indeed work (with limited throughput but full functionality).
What Java version are you running on the workstation? I have not been able to get ASDM (on any ASA) to work with the latest "Java 9" (1.9) update and have had to revert to 1.8.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 01:29 AM
Marvin,
I've been using Java 1.8.0_151 and I also tried Java 1.8.0_73, but it won't work with either. I've also tried it on several freshly built PCs, both Windows 7 and Windows 10, but it just won't work. From the firewall logs I can see the ASDM client connecting and I can see the SSL lib error, even though there are matching ciphers.
So you can definitely confirm that you can download the Cisco ASAv from CCO, build the appliance in VMware ESXI and run it without the application of any licence and it should work, albeit with limited throughput (which is all I need)?
Thanks,
Dom.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 04:17 AM - edited 11-13-2017 04:18 AM
Yes, I confirm it works with the combination you asked.
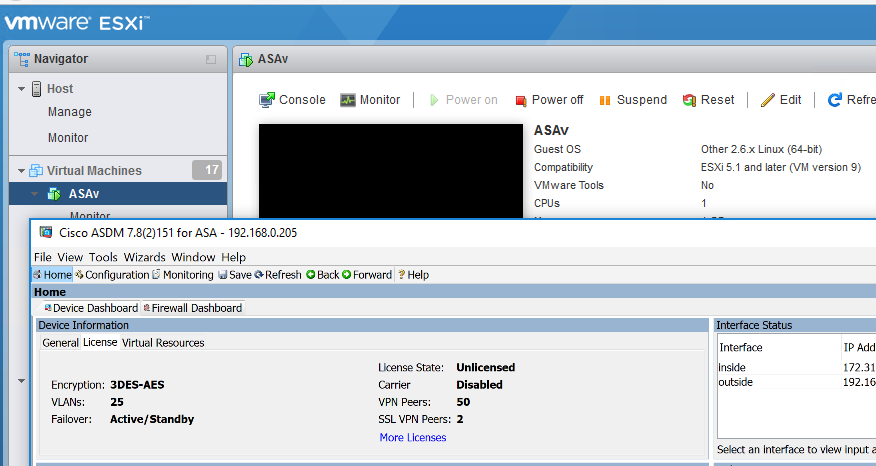
Here is a screenshot of my unlicensed ASAv running on my ESXi 6.0 Update 3 host being managed by ASDM on Windows 10:
asav# show ver
Cisco Adaptive Security Appliance Software Version 9.8(1)7
Firepower Extensible Operating System Version 2.2(1.51)
Device Manager Version 7.8(2)151
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 04:38 AM
Thanks Marvin,
How very odd. The only difference I can see is that you are running 9.8.1(7), whereas i'm running 9.8(2).
I'll try dropping back to the release you are using and see if that works.
Thanks for taking your time to respond. At least I know that it's definitely not a licencing issue.
As an aside, I seem to be able to configure the firewall fine from CLI, it's just the ASDM that doesn't want to play.
Cheers,
Dom
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide