- Cisco Community
- Technology and Support
- Security
- Network Security
- Unsure of how exactly an ASA inspects traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Unsure of how exactly an ASA inspects traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2013 04:07 PM - edited 03-11-2019 07:47 PM
I am running a virtual ASA setup in GNS3. Using a loopback interface, I have ASDM running on my laptop that is connecting into my ASA firewall.
I am trying to ping from 192.168.1.1 (dhcp assigned to PC1) in the "inside" zone, to 192.168.2.50 (server 2 in "dmz" zone - security level 50).
The topology is as follows (I blocked out the made-up public range I'm using so as not to involk a real-life user somewhere - but that shouldn't matter in this scenario):

I have left all of the access rules as default:
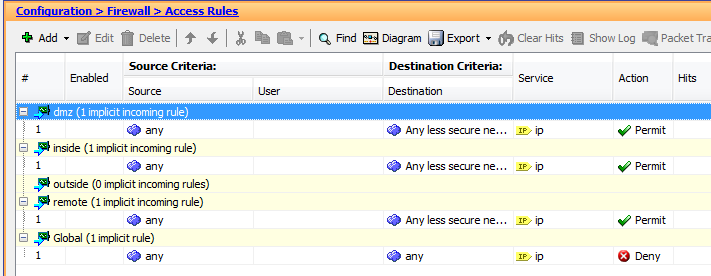
When I ping (the PCs are really VPCS machines) I can see that the ping gets through from "inside" to "dmz", but not BACK. I understand that going from security level 50 to 100 is not allowed - however I thought that the firewall would INSPECT the traffic and make sure that return traffic would be allowed if it was initiated from the "inside" zone.
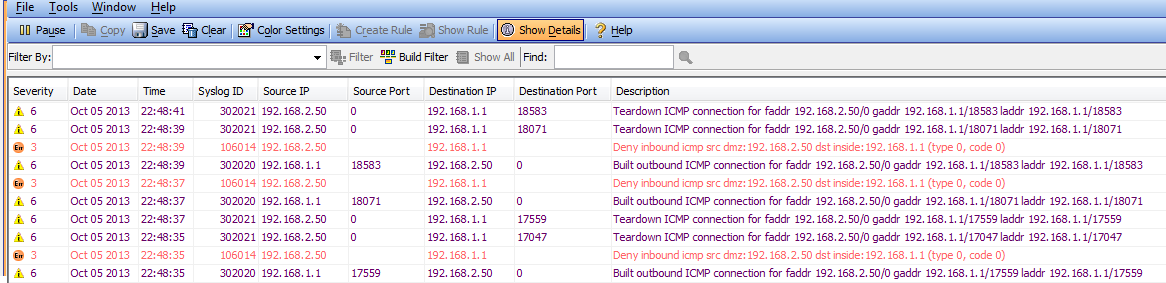
I'm not sure I'm reading these logs correctly. I can provide CLI output of the firewall if requested. I fairly sure this is something fundamental that I'm misunderstanding.
Can any help explain why my ping is failing? Thanks in advance
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2013 05:14 PM
Hi,
Are you sure you have enable ICMP Inspection?
This is NOT enabled by default on the Cisco firewalls
You should add something like (if you are using the default inspections/configurations)
policy-map global_policy
class inspection_default
inspect icmp
inspect icmp error
Alternative is to directly insert the old format commands that will apply the same configurations
fixup protocol icmp
fixup protocol icmp error
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2013 08:42 AM
Unfortunately that didn't work. I have had to explicitly configure access rules allowing ICMP and DNS through:

I have literally only just started my journey into firewalls and I wanted to get this lab up and running as a starting point.
Based on what I learned in CCNA Security your suggestion seems to be correct. I'm sure I'm just applying it incorrectly because of my lack of understanding at this point.
Once I learn more and figure it out, I will come back and update this thread.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2013 09:08 AM
Hi,
Well there shouldnt be many things that cant prevent ICMP from working.
Maybe you can share you current configuration in CLI format for us to go through.
- Jouni
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide




