- Cisco Community
- Technology and Support
- Networking
- Switching
- lan to lan with asa5506 on the same phisical network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2017 05:43 AM - edited 03-08-2019 12:56 PM
Hi,
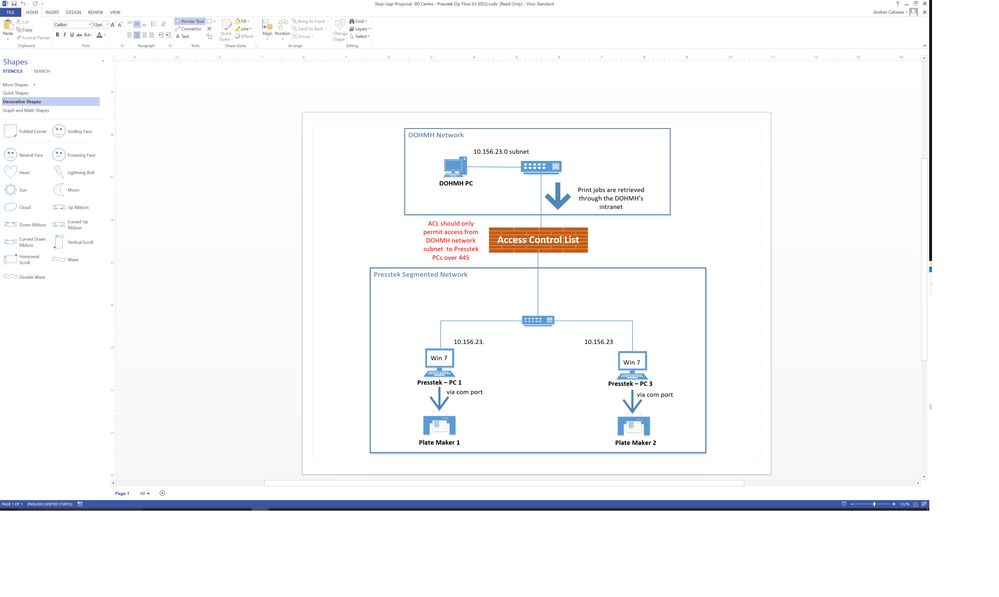
I am a newbie at configuring ASA's and trying to setup a Cisco ASA 5506 for the work flow on the attached image. If anyone could please recommend the best way to setup this ASA to Deny all traffic from LAN PC to Presstek PCs with the exception of port 445 for SMB file transfer. The Presstek computers will have static IP's on the same LAN subnet but they will be connected to the ASA ports and not LAN switch. If you need further info or need me to clarify certain things please let me know. Thanks
Solved! Go to Solution.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2017 12:24 PM
Not helpful. Can you try telnet ?
And where the IP 10.156.23.1 is configured?
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2017 06:13 AM
Well for this test setup I have here right now I don't have the 10.156.23.1 ip configured anywhere. BUt once firewall is installed in production it will be able to communicate with 23.1
Please see the diagram below on the sites network layout and where the new ASA will most likely be connected too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2017 11:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 05:54 AM
Hi,
Are you available for anymore suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 06:29 AM
I am out of idea here. As you could see that Firewall is not blocking the traffic. IP addressing is not a problem as your firewall is on transparent mode. You also said that server is listening on the required service port.
Change the firewall to routed mode is an option but this is not necessary actually. Firewall is supposed to work in both ways.
You can try to install Wireshark on server and then run some tests just to see if packet is getting to the server and if something interesting may show up.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 06:37 AM
Ok what in the config makes the firewall into transparent mode? Can you show me in the config below?
80Centre-FL-ASA-1# sh run
: Saved
:
: Serial Number: JAD21260FF5
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
:
ASA Version 9.7(1)4
!
hostname 80Centre-FL-ASA-1
domain-name health.dohmh.nycnet
enable password $sha512$5000$614vemnZqQcfOfmiKv+YsQ==$4oqF99AoyBNdRBqxtB/e3Q== pbkdf2
names
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 10.156.23.126 255.255.255.128
!
interface GigabitEthernet1/2
nameif inside_1
security-level 100
no ip address
!
interface GigabitEthernet1/3
nameif inside_2
security-level 100
no ip address
!
interface GigabitEthernet1/4
nameif inside_3
security-level 100
no ip address
!
interface GigabitEthernet1/5
nameif inside_4
security-level 100
no ip address
!
interface GigabitEthernet1/6
nameif inside_5
security-level 100
no ip address
!
interface GigabitEthernet1/7
nameif inside_6
security-level 100
no ip address
!
interface GigabitEthernet1/8
nameif inside_7
security-level 100
no ip address
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone EST -5
dns server-group DefaultDNS
domain-name health.dohmh.nycnet
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any1
subnet 0.0.0.0 0.0.0.0
object network obj_any2
subnet 0.0.0.0 0.0.0.0
object network obj_any3
subnet 0.0.0.0 0.0.0.0
object network obj_any4
subnet 0.0.0.0 0.0.0.0
object network obj_any5
subnet 0.0.0.0 0.0.0.0
object network obj_any6
subnet 0.0.0.0 0.0.0.0
object network obj_any7
subnet 0.0.0.0 0.0.0.0
object network outside-network
subnet 10.156.23.0 255.255.255.128
object network DOHMH-LAN
subnet 10.156.23.0 255.255.255.128
description DOHMH-LAN
object network 10.156.23.33
host 10.156.23.33
description Presstek PC1
object network 10.156.23.88
host 10.156.23.88
description Presstek PC3
object network ASA-IP
host 10.156.23.126
object-group service DM_INLINE_SERVICE_1
service-object tcp destination eq 137
service-object tcp destination eq 138
service-object tcp destination eq 445
service-object tcp destination eq ftp
service-object tcp destination eq netbios-ssn
service-object udp destination eq 139
service-object udp destination eq netbios-dgm
service-object udp destination eq netbios-ns
service-object udp destination eq 445
object-group network Presstek_PCs
description Presstek PCs
network-object object 10.156.23.33
network-object object 10.156.23.88
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_1 object DOHMH-LAN object-group Presstek_PCs
access-list outside_access_in extended permit icmp any any
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside_1 1500
mtu inside_2 1500
mtu inside_3 1500
mtu inside_4 1500
mtu inside_5 1500
mtu inside_6 1500
mtu inside_7 1500
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside_1
icmp permit any inside_2
icmp permit any inside_3
icmp permit any inside_4
icmp permit any inside_5
icmp permit any inside_6
icmp permit any inside_7
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 10.156.23.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
http server enable
http 0.0.0.0 0.0.0.0 outside
http 0.0.0.0 0.0.0.0 inside_1
http 0.0.0.0 0.0.0.0 inside_2
http 0.0.0.0 0.0.0.0 inside_3
http 0.0.0.0 0.0.0.0 inside_4
http 0.0.0.0 0.0.0.0 inside_5
http 0.0.0.0 0.0.0.0 inside_6
http 0.0.0.0 0.0.0.0 inside_7
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 10.242.184.0 255.255.255.0 outside
ssh 10.151.16.128 255.255.255.128 outside
ssh 10.227.255.128 255.255.255.128 outside
ssh 10.242.127.240 255.255.255.240 outside
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
username dohadmin password $sha512$5000$/HmhJRWXvFcwjEZLMQmSig==$NFSV9Tv26wr9Q6CteB5w8Q== pbkdf2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:531b730caa54f6407795b9f6e035a8b8
: end
Capture Results after running telnet from DOHMH PC 10.156.23.50 to Presstek machine 10.156.23.88
80Centre-FL-ASA-1# sh capture cap2
28 packets captured
1: 02:30:06.695062 10.156.23.126.443 > 10.156.23.50.49717: P 3416216968:3416218377(1409) ack 3946438249 win 32768
2: 02:30:06.695093 10.156.23.126.443 > 10.156.23.50.49717: P 3416218377:3416219786(1409) ack 3946438249 win 32768
3: 02:30:06.695123 10.156.23.126.443 > 10.156.23.50.49717: P 3416219786:3416221151(1365) ack 3946438249 win 32768
4: 02:30:06.695535 10.156.23.50.49717 > 10.156.23.126.443: . ack 3416221151 win 64240
5: 02:30:06.695596 10.156.23.126.443 > 10.156.23.50.49717: P 3416221151:3416222080(929) ack 3946438249 win 32768
6: 02:30:06.813358 arp who-has 10.156.23.1 tell 10.156.23.50
7: 02:30:06.827319 10.156.23.126.443 > 10.156.23.50.49717: P 3416221151:3416222080(929) ack 3946438249 win 32768
8: 02:30:06.827593 10.156.23.50.49717 > 10.156.23.126.443: . ack 3416222080 win 63311
9: 02:30:07.328291 10.156.23.50.137 > 10.156.23.127.137: udp 50
10: 02:30:07.468557 arp who-has 10.156.23.1 tell 10.156.23.50
11: 02:30:08.092738 10.156.23.50.137 > 10.156.23.127.137: udp 50
12: 02:30:08.467001 arp who-has 10.156.23.1 tell 10.156.23.50
13: 02:30:08.877029 arp who-has 10.156.23.1 tell 10.156.23.50
14: 02:30:09.465384 arp who-has 10.156.23.1 tell 10.156.23.50
15: 02:30:09.934110 arp who-has 10.156.23.88 tell 10.156.23.50
16: 02:30:10.463797 arp who-has 10.156.23.1 tell 10.156.23.50
17: 02:30:10.463812 arp who-has 10.156.23.88 tell 10.156.23.50
18: 02:30:11.462256 arp who-has 10.156.23.88 tell 10.156.23.50
19: 02:30:12.070629 10.156.23.50.137 > 10.156.23.127.137: udp 50
20: 02:30:12.819476 arp who-has 10.156.23.1 tell 10.156.23.50
21: 02:30:12.835070 10.156.23.50.137 > 10.156.23.127.137: udp 50
22: 02:30:12.944363 arp who-has 10.156.23.88 tell 10.156.23.50
23: 02:30:13.458945 arp who-has 10.156.23.1 tell 10.156.23.50
24: 02:30:13.458960 arp who-has 10.156.23.88 tell 10.156.23.50
25: 02:30:13.599425 10.156.23.50.137 > 10.156.23.127.137: udp 50
26: 02:30:14.383998 arp who-has 10.156.23.1 tell 10.156.23.50
27: 02:30:14.457480 arp who-has 10.156.23.88 tell 10.156.23.50
28: 02:30:14.956646 arp who-has 10.156.23.1 tell 10.156.23.50
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 06:54 AM
This is not shown on the running-config. But you can change this buy issuing the command "no firewall transparent "
But bear in mind that this will change your environment completely.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 07:04 AM
No that's fine I don't want to change it and mess it up from what it is now. I just thought there was a way to tell your router is in transparent mode. Ok I installed wireshark on my laptop which has IP 10.156.23.88 and its suppose to mimic one of the Presstek computers on site. I am running a ping -t and telnet from DOHMH PC 10.156.23.50 and this are the results am seeing with wireshark. To me it seems like the packets are getting to 23.88 it just doesn't know how to get back to the source. Am I correct? Being that this is a test setup offline do I need to add a static route on my windows PC 23.88 so that it knows how to get back to the source? Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 07:13 AM
This is not necessary as the communication happens on layer 2 mode only.
How does the AP addressing on the PCs looks like? Which mask are you using? On firewall your are using 255.255.255.128, does the PCs has the same mask?
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 07:33 AM
using the same mask on both laptops
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 07:40 AM
Change the security level of outside interface to 100.
And add the command same- security-traffic permit inter-interface
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 07:46 AM
ok I changed the security level to 100 and also had that command already in config. Still get same results when I ping and telnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 07:54 AM
It seems that the ARP resquest from on host is not getting in to the destination host.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 08:01 AM
Run the command :
show mac-address-table
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 09:03 AM
when I run the mac address command it doesn't show anything.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide