- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Multiple Site to Site VPN on single cisco Router.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2013 11:09 PM - edited 03-07-2019 03:44 PM
Hello Network Admins,
I need your help here configuring additional Site to Site VPN on Cisco router.
Note: Site-A = Head office
Site-B= Branch office -----------> Public IP : 87.101.54.74
Site-C= Branch office -----------> Public IP : 87.101.80.94
Site to Site VPN is configured between Site A to B and Site A to C. However, I am trying to configure Site to Site VPN from Branch office to Branch office Site-B to Site-C. Here is my existing Site to Site VPN running configuration which is connected to head office. Please let me know what can be done to configure branch office to Branch office? Thank you.
Site B#show run
Building configuration...
Current configuration : 2672 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname SIT
!
boot-start-marker
boot system flash flash:c2800nm-advsecurityk9-mz.124-15.T9.bin
boot system flash flash:c2800nm-ipbase-mz.124-15.T10.bin
boot-end-marker
!
logging buffered 51200 warnings
enable secret 5 $1$UC784zH75YQO..fhY6S.ar0
enable password asdf
!
no aaa new-model
dot11 syslog
!
!
ip cef
no ip dhcp use vrf connected
!
ip dhcp pool DSL
network 10.11.4.0 255.255.255.0
default-router 10.11.4.1
dns-server 208.67.222.222
!
!
ip domain name yourdomain.com
!
multilink bundle-name authenticated
!
!
!
!
!
username admin privilege 15 secret 5 $ghjikhggfffd
archive
log config
hidekeys
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key ijklmnopq address 87.101.158.218 no-xauth
!
!
crypto ipsec transform-set VPN_ITC_TS esp-aes esp-sha-hmac
!
crypto map VPN_ITC 10 ipsec-isakmp
set peer 87.101.158.218
set transform-set VPN_ITC_TS
match address 135
!
!
!
!
class-map match-any Servers-List
match access-group 190
!
!
policy-map Servers
class Servers-List
bandwidth percent 50
!
!
!
!
interface FastEthernet0/0
description WAN ITC
bandwidth 2048
ip address 87.101.54.74 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map VPN_ITC
service-policy output Servers
!
interface FastEthernet0/1
description LAN ITC
ip address 10.11.4.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 87.101.54.73
ip route 87.101.158.216 255.255.255.252 87.101.54.73
ip route 192.168.0.0 255.255.0.0 87.101.54.73
!
!
ip http server
ip http access-class 23
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 138 interface FastEthernet0/0 overload
!
access-list 135 permit ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 deny ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 permit ip 10.11.4.0 0.0.0.255 any
access-list 190 remark List of Servers to be assigned QOS
access-list 190 permit ip any host 192.168.50.1
access-list 190 permit ip any host 192.168.50.13
access-list 190 permit ip any host 192.168.50.15
access-list 190 permit ip any host 192.168.50.21
access-list 190 permit ip any host 192.168.50.22
access-list 190 permit ip any host 192.168.50.24
!
!
!
!
control-plane
!
!
line con 0
login local
line aux 0
line vty 0 4
login local
transport input telnet
!
scheduler allocate 20000 1000
!
end
Site-C configuration: -
Current configuration : 2859 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname SIT
!
boot-start-marker
boot system flash flash:c2800nm-advsecurityk9-mz.124-15.T9.bin
boot system flash flash:c2800nm-ipbase-mz.124-15.T10.bin
boot-end-marker
!
logging buffered 51200 warnings
enable password 7 0101565446764F1E2837253221
!
no aaa new-model
dot11 syslog
!
!
ip cef
no ip dhcp use vrf connected
!
ip dhcp pool DSL
network 10.11.10.0 255.255.255.0
default-router 10.11.10.1
dns-server 208.67.222.222
!
!
ip domain name yourdomain.com
!
multilink bundle-name authenticated
!
!
!
!
!
username awalnet privilege 15 secret 5 $1$O9C6$hGhgghd4.L7ULalS7Wt/
archive
log config
hidekeys
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key 5O15B67n address 87.101.158.218 no-xauth
!
!
crypto ipsec transform-set VPN_ITC_TS esp-aes esp-sha-hmac
!
crypto map VPN_ITC 10 ipsec-isakmp
set peer 87.101.158.218
set transform-set VPN_ITC_TS
match address 135
!
!
!
!
class-map match-any Servers-List
match access-group 190
!
!
policy-map Servers
class Servers-List
bandwidth percent 50
!
!
!
!
interface FastEthernet0/0
description WAN Link to ITC
bandwidth 2048
ip address 87.101.80.94 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map VPN_ITC
service-policy output Servers
!
interface FastEthernet0/1
description LAN
ip address 10.11.10.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex full
speed 100
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 87.101.80.93
ip route 87.101.158.216 255.255.255.252 87.101.80.93
ip route 192.168.0.0 255.255.0.0 87.101.80.93
!
!
ip http server
ip http access-class 23
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 138 interface FastEthernet0/0 overload
!
access-list 135 permit ip 10.11.10.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 deny ip 10.11.10.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 permit ip 10.11.10.0 0.0.0.255 any
access-list 190 remark List of Servers to be assigned QOS
access-list 190 permit ip any host 192.168.50.1
access-list 190 permit ip any host 192.168.50.13
access-list 190 permit ip any host 192.168.50.15
access-list 190 permit ip any host 192.168.50.21
access-list 190 permit ip any host 192.168.50.22
access-list 190 permit ip any host 192.168.50.24
!
!
!
!
control-plane
!
!
line con 0
login local
line aux 0
line vty 0 4
privilege level 15
login local
transport input telnet
line vty 5 15
access-class 23 in
privilege level 15
login local
transport input telnet
!
scheduler allocate 20000 1000
!
end
Note: IPs and passwords are edited just for understanding. Thank you.
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 12:42 AM
Dear Friend,
138 is not for IPSec its for NAT. So there wont be any downtime.
Plz rate if helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2013 11:28 PM
The current configuration on Site-B is for Site-A right ? i dont see any crypto configured for SITE C.
Do you want the complete configuration for SITE-B and SITE-C ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2013 11:34 PM
Hello John,
Yes sir, Could you please help me how to add one more Site to Site VPN on cisco router. Actually I was able to configure sote tp site VPN from Site A to Site C and Site B to Site C. Now I want to configure Site to Site VPN from Site-B to Site-C. Help needed. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2013 11:42 PM
Its easy, i will leave the IPs for you to fill (i have bolded them in configuration where you need to fill)
Site-B
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key 0 abc123 address
access-list 101 per ip
crypto ipsec transform-set VPN_ITC_TS esp-aes esp-sha-hmac
crypto map VPN_ITC 10 ipsec-isakmp
set peer 87.101.158.218
set transform-set VPN_ITC_TS
match address 135
crypto map VPN_ITC 20 ipsec-isakmp
set peer
set transform-set VPN_ITC_TS
match address 101
The catch is, you cant assign more then 1 crypto map to interfaces. You will need to add statements to your crypto map like we do in route-maps. Above, i created another line number 20 and configured the parameters there
Let me know if you are clear till now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 12:05 AM
Hello John,
Thank you so much. I will give it a try. What you are trying to tell is I cannot assign more than 1 crypto map to Interface. At present crypto map is "VPN_ITC" on both ends. So it should not be a problem. Actually I am confused with natting and Access list at the moment. Please have a look at the following commands. Please educate me over here.
"ip nat inside source list 138 interface FastEthernet0/0 overload"
access-list 135 permit ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 deny ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 permit ip 10.11.4.0 0.0.0.255 any
access-list 190 remark List of Servers to be assigned QOS
access-list 190 permit ip any host 192.168.50.1
access-list 190 permit ip any host 192.168.50.13
access-list 190 permit ip any host 192.168.50.15
access-list 190 permit ip any host 192.168.50.21
access-list 190 permit ip any host 192.168.50.22
access-list 190 permit ip any host 192.168.50.24
Here note that in access-list 138 there is deny and permit statment. However, I am trying to commincate between 10.11.4.0 subnet to 10.11.10.0. So do I need to add one more access list as you mentioned by changing access list number 101. Orelese Shall I add this existing command and keep access list number same as 138
"access-list 138 deny ip 10.11.4.0 255.255.255.0 10.11.10.0 255.255.255.0"
Just confused with access list part. Okay in case if access list number changed to 101 as you mentioned. Do i need to configure.
"
ip nat inside source list 101 interface FastEthernet0/0 overload" Is that possible. Let me know. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 12:16 AM
Dear Friend,
Very good question and here is the answer
1) In site to site vpn, ipsec forms a tunnel (just like gre but you dont actually see the interface or cant configure it). So when you are communicating through site to site vpn, both LAN subnets remain unnatted since they are being encapsulated inside ipsec tunnel. I will break down you nat/access-list statment to explain what each line is doing
access-list 138 deny ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255 (if traffic is going from my lan to Site A LAN. dont NAT it, since its going via ipsec tunnel)
access-list 138 permit ip 10.11.4.0 0.0.0.255 any (but if the traffic is going anywhere else, essentially internet, then NAT it)
then comes the NAT statement
ip nat inside source list 138 interface FastEthernet0/0 overload
Now keep in mind that in your existing configuration you have 2 access-list working for 2 different purpose
access-list 138 is for nat
access-list 135 is for IPSec
In configuration fro SITe-B to Site-C, we have created access-list 101 for IPSEC. Now we need to edit access-list 138. Do this
ip access-list extended 138
15 deny ip
Let me know if it clears
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 12:32 AM
Hello John,
Thank you so much. Everything is clear. if possible could you please explain the following statment.
"ip access-list extended 138
15 deny ip
My question. if we edit access-list 138
Will the tunnel go Down from Site A to Site B. I want to keep both tunnels up at the same time "Site A to Site-B and, Site B to Site-C which is after configuration. Let me know. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 12:42 AM
Dear Friend,
138 is not for IPSec its for NAT. So there wont be any downtime.
Plz rate if helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 12:46 AM
Hello John,
You are the saver. Now I understand. I will try this configuration exactly after 1 hr 15 mins. and let you know the result. Thank you. You were very helpfull.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 01:09 AM
You are most welcome my friend
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 01:10 AM
Hello lili,
you can apply named access-list to your configuration as I mention in the below, also this configuration exclude the LAN to LAN of VPN connection and allow the NAT traffic.
ip access-list extended NAT
deny ip 10.11.10.0 0.0.0.255 192.168.0.0 0.0.255.255 ......... (LAN_to_LAN of VPN)
permit ip 10.11.10.0 0.0.0.255 any ..................... ( LAN ip address for NAT)
your confgiuraiotn for the NAT will be as a below:
ip nat inside source list NAT interface GigabitEthernet0/0 overload
you will use the same ACL for the VPN connection as you configured it.
access-list 135 permit ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 07:38 PM
Hello Hardi,
Thank you so much for the reply. Actually I am tryin to configure from Site B to Site C. Please have a look at the configuration. Please let me know what could be wrong. Thank you,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 07:15 PM
Hello John,
I tried the configuration as you said. Please have a look at site-B and Site-C config. Let me know what could be wrong. The config didn't work
Site B#show run
Building configuration...
Current configuration : 2672 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname SITE-B
!
boot-start-marker
boot system flash flash:c2800nm-advsecurityk9-mz.124-15.T9.bin
boot system flash flash:c2800nm-ipbase-mz.124-15.T10.bin
boot-end-marker
!
logging buffered 51200 warnings
enable secret 5 $1$UC784zH75YQO..fhY6S.ar0
enable password asdf
!
no aaa new-model
dot11 syslog
!
!
ip cef
no ip dhcp use vrf connected
!
ip dhcp pool DSL
network 10.11.4.0 255.255.255.0
default-router 10.11.4.1
dns-server 208.67.222.222
!
!
ip domain name yourdomain.com
!
multilink bundle-name authenticated
!
!
!
!
!
username admin privilege 15 secret 5 $ghjikhggfffd
archive
log config
hidekeys
!
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key ijklmnopq address 87.101.158.218 no-xauth
crypto isakmp key l24554bLJK address 87.101.80.94 no-xauth
!
!
crypto ipsec transform-set VPN_ITC_TS esp-aes esp-sha-hmac
!
crypto map VPN_ITC 10 ipsec-isakmp
set peer 87.101.158.218
set transform-set VPN_ITC_TS
match address 135
crypto map VPN_ITC 20 ipsec-isakmp
set peer 87.101.80.94
set transform-set VPN_ITC_TS
match address 101
!
!
!
!
!
!
interface FastEthernet0/0
description WAN ITC
bandwidth 2048
ip address 87.101.54.74 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map VPN_ITC
service-policy output Servers
!
interface FastEthernet0/1
description LAN ITC
ip address 10.11.4.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 87.101.54.73
ip route 10.11.4.0 255.255.255.0 87.101.54.73
ip route 87.101.158.216 255.255.255.252 87.101.54.73
ip route 192.168.0.0 255.255.0.0 87.101.54.73
!
!
ip http server
ip http access-class 23
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 138 interface FastEthernet0/0 overload
!
access-list 101 permit ip 10.11.4.0 0.0.0.255 10.11.10.0 0.0.0.255
access-list 135 permit ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 deny ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 permit ip 10.11.4.0 0.0.0.255 any
!
!
!
!
control-plane
!
!
line con 0
login local
line aux 0
line vty 0 4
login local
transport input telnet
!
scheduler allocate 20000 1000
!
end
Branch office Site-C : -
Site C#show run
Building configuration...
Current configuration : 2859 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname SITE-C
!
boot-start-marker
boot system flash flash:c2800nm-advsecurityk9-mz.124-15.T9.bin
boot system flash flash:c2800nm-ipbase-mz.124-15.T10.bin
boot-end-marker
!
logging buffered 51200 warnings
enable password 7 0101565446764F1E2837253221
!
no aaa new-model
dot11 syslog
!
!
ip cef
no ip dhcp use vrf connected
!
ip dhcp pool DSL
network 10.11.10.0 255.255.255.0
default-router 10.11.10.1
dns-server 208.67.222.222
!
!
ip domain name yourdomain.com
!
multilink bundle-name authenticated
!
!
!
!
!
username awalnet privilege 15 secret 5 $1$O9C6$hGhgghd4.L7ULalS7Wt/
archive
log config
hidekeys
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key 5O15B67n address 87.101.158.218 no-xauth
crypto isakmp key l24554bLJK address 87.101.54.74 no-xauth
!
!
crypto ipsec transform-set VPN_ITC_TS esp-aes esp-sha-hmac
!
crypto map VPN_ITC 10 ipsec-isakmp
set peer 87.101.158.218
set transform-set VPN_ITC_TS
match address 135
crypto map VPN_ITC 20 ipsec-isakmp
set peer 87.101.54.74
set transform-set VPN_ITC_TS
match address 101
!
!
!
!
!
!
interface FastEthernet0/0
description WAN Link to ITC
bandwidth 2048
ip address 87.101.80.94 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map VPN_ITC
!
interface FastEthernet0/1
description LAN
ip address 10.11.10.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex full
speed 100
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 87.101.80.93
ip route 10.11.10.0 255.255.255.0 87.101.80.93
ip route 87.101.158.216 255.255.255.252 87.101.80.93
ip route 192.168.0.0 255.255.0.0 87.101.80.93
!
!
ip http server
ip http access-class 23
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 138 interface FastEthernet0/0 overload
!
access-list 20 permit 212.93.196.0 0.0.0.255
access-list 101 permit ip 10.11.10.0 0.0.0.255 10.11.4.0 0.0.0.255
access-list 135 permit ip 10.11.10.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 deny ip 10.11.10.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 permit ip 10.11.10.0 0.0.0.255 any
!
!
!
!
control-plane
!
!
line con 0
login local
line aux 0
line vty 0 4
privilege level 15
login local
transport input telnet
line vty 5 15
access-class 23 in
privilege level 15
login local
transport input telnet
!
scheduler allocate 20000 1000
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 07:37 PM
Here are atta chments.
chments. 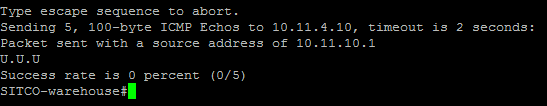
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2013 08:00 PM
The issue is in the ACL used for address translation. If you look at the ACL used in what you posted you will see that it denies traffic from only one entry in the crypto map. The result is that traffic that is attempting to go to the second entry in the crypto map will be translated.
access-list 138 deny ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 permit ip 10.11.4.0 0.0.0.255 any
if you make it look more like this it should work
access-list 138 deny ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 deny ip 10.11.4.0 0.0.0.255 10.11.4.0 0.0.0.255
access-list 138 permit ip 10.11.4.0 0.0.0.255 any
HTH
Rick
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

