- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Cisco ASA IPv6 Site-to-Site IPSec IKEv2 VPN
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-02-2014 01:27 PM - edited 03-01-2019 05:02 PM
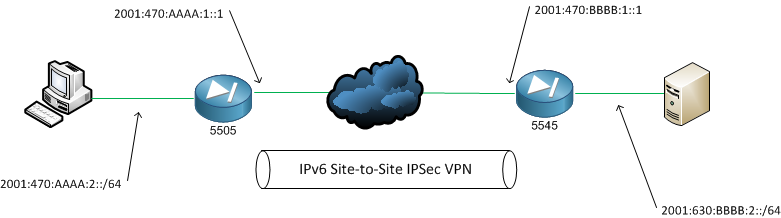
Current Cisco configuration documentation shows the use of 3des encryption and MD5 hashing functions. According to the Cisco document on Next Gen Encryption (NGE) both are listed as ‘avoid’ and ‘legacy’. Using this document the tunnel shown here will used the recommend strength of encryption and hashing, whilst at the same time not crippling my 5505 with computations!!
The configuration of the ASA’s is pretty much identical with the exception of pre-shared key phrases and ACLs needing to be flipped.
The first step is to create the IKE policies. We will be using IKEv2 which was introduced in the ASA 8.4 software release. IKEv2 adds many improvements, one of which that will be visible in the configuration is asymmetric keys.
Configured on both:
! crypto ikev2 policy 1 encryption aes-256 integrity sha256 group 2 prf sha256 lifetime seconds 43200 ! asa(config)# crypto ikev2 enable outside ! crypto ipsec ikev2 ipsec-proposal ikev2_aes256 protocol esp encryption aes-256 protocol esp integrity sha-1 ! |
A tunnel-group is a set of connection polices related to the specified peer. In this config we are utilising a feature of IKEv2, asymmetric authentication methods. For the sake of simplicity either ends will be using pre-shared keys.
The ACL is used to match traffic, which when used with the crypto map below will ensure it is sent down the tunnel.
Configured on the 5505:
! tunnel-group 2001:630:BBBB:1::1 type ipsec-l2l tunnel-group 2001:630:BBBB:1::1 ipsec-attributes ikev2 remote-authentication pre-shared-key 0 th3_5545 ikev2 local-authentication pre-shared-key 0 s3b5_5505 ! access-list acl_l2l_01 extended permit ip 2001:470:AAAA:2::/64 2001:630:BBBB:2::/64 ! |
Configured on the 5545-X:
! tunnel-group 2001:470:AAAA:1::1 type ipsec-l2l tunnel-group 2001:470:AAAA:1::1 ipsec-attributes ikev2 remote-authentication pre-shared-key 0 s3b5_5505 ikev2 local-authentication pre-shared-key 0 th3_5545 ! access-list acl_l2l_01 extended permit ip 2001:630:BBBB:2::/64 2001:470:AAAA:2::/64 ! |
The crypto map draws together all of the above configuration:
- The ACL defines what traffic should be protected by IPSec
- The IKEv2 IPSec proposal allows for the configuration of multiple transform-sets; one of which both peers must agree on. Once agreed the transform-set is used to define of transmitted data is to be protected.
- Specify the ASA interface to apply the crypto map. All traffic passing through the interface will be evaluated against the crypto map.
Configured on both:
! crypto map l2l_01 1 match address acl_l2l_01 crypto map l2l_01 1 set ikev2 ipsec-proposal ikev2_aes256 crypto map l2l_01 interface outside ! |
Now specify for each crypto map, where matching traffic should be sent.
ASA5505:
! crypto map l2l_01 1 set peer 2001:630:BBBB:1::1 ! |
ASA 5545-X:
! crypto map l2l_01 1 set peer 2001:470:AAAA:1::1 ! |
The VPN will not become active until it starts to pass traffic. To test start a ping which will match the ACL of whichever tunnel endpoint is closest, eg from a host on the 2001:470:AAAA:2::/64 subnet:
$ ping6 2001:630:BBBB:2::100
Now check the CLI on each ASA:
ASA5505:
ciscoasa5505# sh crypto ikev2 sa detail
IKEv2 SAs: Session-id:1, Status:UP-ACTIVE, IKE count:1, CHILD count:1 Tunnel-id Local Remote Status Role 255226471 2001:470:aaaa:1::1 2001:630:bbbb:1::1/5 READY INITIATOR Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:2, Auth sign: PSK, Auth verify: PSK Life/Active Time: 43200/149 sec Session-id: 1 Status Description: Negotiation done Local spi: 7A3122706F95C51C Remote spi: 2B17187D4CA841CD Local id: 2001:470:aaaa:1::1 Remote id: 2001:630:bbbb:1::1 Local req mess id: 7 Remote req mess id: 4 Local next mess id: 7 Remote next mess id: 4 Local req queued: 7 Remote req queued: 4 Local window: 1 Remote window: 1 DPD configured for 10 seconds, retry 2 NAT-T is not detected Child sa: local selector 2001:470:aaaa:2::/0 - 2001:470:aaaa:2:ffff:ffff:ffff:ffff/65535 remote selector 2001:630:bbbb:2::/0 - 2001:630:bbbb:2:ffff:ffff:ffff:ffff/65535 ESP spi in/out: 0x28fc953/0x5d23b1e AH spi in/out: 0x0/0x0 CPI in/out: 0x0/0x0 Encr: AES-CBC, keysize: 256, esp_hmac: SHA96 ah_hmac: None, comp: IPCOMP_NONE, mode tunnel |
ASA5545-X
Session-id:6, Status:UP-ACTIVE, IKE count:1, CHILD count:1 Tunnel-id Local Remote Status Role 2203917 2001:630:bbbb:1::1/5 2001:470:aaaa:1::1 READY RESPONDER Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:2, Auth sign: PSK, Auth verify: PSK Life/Active Time: 43200/40 sec Session-id: 6 Status Description: Negotiation done Local spi: 2B17187D4CA841CD Remote spi: 7A3122706F95C51C Local id: 2001:630:bbbb:1::1 Remote id: 2001:470:aaaa:1::1 Local req mess id: 0 Remote req mess id: 2 Local next mess id: 0 Remote next mess id: 2 Local req queued: 0 Remote req queued: 2 Local window: 1 Remote window: 1 DPD configured for 10 seconds, retry 2 NAT-T is not detected Child sa: local selector 2001:630:bbbb:2::/0 - 2001:630:bbbb:2:ffff:ffff:ffff:ffff/65535 remote selector 2001:470:aaaa:2::/0 – 2001:470:aaaa:2:ffff:ffff:ffff:ffff/65535 ESP spi in/out: 0x5d23b1e/0x28fc953 AH spi in/out: 0x0/0x0 CPI in/out: 0x0/0x0 Encr: AES-CBC, keysize: 256, esp_hmac: SHA96 ah_hmac: None, comp: IPCOMP_NONE, mode tunnel |
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Seb,
Is it possible to run native ipv6 ipsec site-to-site vpn on cisco ASAv running this version of code:
Cisco Adaptive Security Appliance Software Version 9.8(2)20
Firepower Extensible Operating System Version 2.2(2.66)
Device Manager Version 7.9(2)152
Thanks.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: