- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IKEv2 S2S between ISR 886VA and ASA 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 02:46 AM - edited 03-12-2019 05:25 AM
Hello,
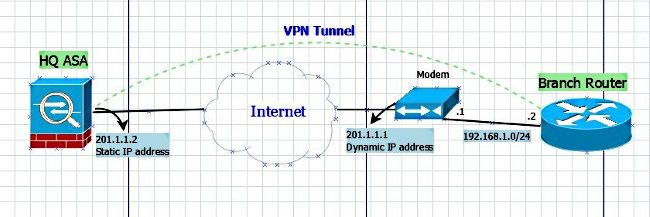
I try to configure the IKEv2 tunnel between ASA 5510 and ISR 886VA using this article, scenario one. I have configured it, but i have a few questions:
1) what is the address 10.10.10.1 ? there is no such IP address on the scheme:
2) how can i define which traffic to send through the tunnel? For example, there is a network behind the ASA 10.255.10.0/24, I would like to access it from ISR network 10.254.1.0/24, but I don't need to encrypt the traffic to network 10.255.30.0/24.
My scheme:
Thank you in advance!
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 01:52 AM
unfortunately it didn't help.
from ASA:
ASA1# traceroute 10.254.1.133
Type escape sequence to abort.
Tracing the route to 10.254.1.133
1 lan.fra1.domain.local (201.1.1.1) 0 msec 0 msec 0 msec
2 * * *
3 * * *
4 * * *
5 * * *
from Router:
#traceroute 10.255.10.160
Type escape sequence to abort.
Tracing the route to 10.255.10.160
VRF info: (vrf in name/id, vrf out name/id)
1 XXX.XXX.XXX.XXX 20 msec 16 msec 20 msec
2 XXX.XXX.XXX.XXX !H !H !H
the clients have the same issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 03:20 AM
Ta
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 04:32 AM
@Rob Ingram wrote:
Can you please provide some debug output "debug crypto ikev2"?
Ta
debug shows nothing. it is silent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 06:23 AM
If nothing is in the debug of the router either traffic isn't matching the acl and therefore triggering the tunnel or the crypto map is enabled on the wrong interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 06:58 AM
yes, I enabled the debug and then generated a traffic but nothing has been shown.
You saw my config. The ACL is good, but interface... I enable all maps or rules on the Dialer0 interface. Also I tried to enable it on VLAN1 interface - still the same: no traceroute, no logging...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 07:10 AM
You previously run a traceroute from the router itself, that doesn't guarantee that the source IP address is within the crypto map subnet. Can you ping and traceroute 10.255.10.x from a device within the range 10.254.1.x. Please provide debugs and outputs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 08:32 AM
I did tracert from a Windows client in 10.255.10.0/24 and another client from 10.254.1.0/24 too - always the same. It comes to router or ASA and stops. and there is no any debug log too while the tracert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 08:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 08:47 AM
ISR#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is YYY.YYY.YYY.YYY to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via YYY.YYY.YYY.YYY
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
C 10.254.1.0/24 is directly connected, Vlan1
L 10.254.1.1/32 is directly connected, Vlan1
C 10.254.2.0/24 is directly connected, Vlan2
L 10.254.2.1/32 is directly connected, Vlan2
S 10.254.10.0/24 [1/0] via 10.254.1.4
S 10.255.9.11/32 [1/0] via 10.254.1.8
XX.0.0.0/32 is subnetted, 1 subnets
C XXX.XXX.XXX.XXX is directly connected, Dialer0
YY.0.0.0/32 is subnetted, 1 subnets
C YYY.YYY.YYY.YYY is directly connected, Dialer0
172.66.0.0/24 is subnetted, 1 subnets
S 172.66.0.0 [1/0] via 10.254.1.4
192.168.178.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.178.0/24 is directly connected, Vlan3
L 192.168.178.1/32 is directly connected, Vlan3
In my previous Router's config I removed some VLANs, thinking they are not matter.
ASA1# sh route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is ZZZ.ZZZ.ZZZ.ZZZ to network 0.0.0.0
C ZZZ.ZZZ.ZZZ.ZZZ 255.255.255.248 is directly connected, WAN
S 172.65.0.0 255.255.255.0 [1/0] via 10.255.10.1, LAN-MSP
S 10.100.0.0 255.255.255.0 [1/0] via 10.255.10.1, LAN-MSP
S 10.255.10.76 255.255.255.255 [1/0] via 10.255.10.1, LAN-MSP
S 10.144.90.11 255.255.255.255 [1/0] via 10.255.10.1, LAN-MSP
S 10.249.0.0 255.255.255.0 [1/0] via 10.255.10.1, LAN-MSP
C 10.255.3.0 255.255.255.0 is directly connected, management
S 10.255.9.0 255.255.255.0 [1/0] via 10.255.3.1, management
C 10.255.10.0 255.255.255.0 is directly connected, LAN-MSP
S* 0.0.0.0 0.0.0.0 [1/0] via ZZZ.ZZZ.ZZZ.ZZZ, WAN
don't think of the 172 networks. it's a rudiment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 08:58 AM
It references "ip nat inside source list 101 interface Dialer0 overload" but acl 101 is not in the config.
I assume you can ping the public ip address of the ASA from the router and the routers' lan?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2018 01:57 AM
I would like to clean router's config. for example a think of where to move the current VPN to remove the portforwarding forever. I will reconfigure the Router a little bit and then send the full config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2018 09:15 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2018 12:35 PM
interface Vlan1
description LAN
no crypto map vpn
!
interface Dialer0
description VDSL TELEKOM
crypto map vpn
!
ip access-list extended vpn
permit ip host 10.254.1.1 187.XXX.XXX.XX1
!
ip access-list ext 101
1 deny ip host 10.254.1.1 187.XXX.XXX.XX1
#debug crypto ikev2
#ping 187.XXX.XXX.XX1 source 10.254.1.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2018 06:24 AM
@a.alekseev wrote:
!
interface Vlan1
description LAN
no crypto map vpn
!
interface Dialer0
description VDSL TELEKOM
crypto map vpn
!
ip access-list extended vpn
permit ip host 10.254.1.1 187.XXX.XXX.XX1
!
ip access-list ext 101
1 deny ip host 10.254.1.1 187.XXX.XXX.XX1
#debug crypto ikev2
#ping 187.XXX.XXX.XX1 source 10.254.1.1
ping 187.XXX.XXX.XX1 source 10.254.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 187.XXX.XXX.XX1, timeout is 2 seconds: Packet sent with a source address of 10.254.1.1 .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 28/31/32 ms
Ok.
But when I ping any hosts behind the ASA - it still doesn't work:
tracert 10.255.10.160 Tracing route to 10.255.10.160 over a maximum of 30 hops 1 1 ms 1 ms 1 ms 10.254.1.1 2 18 ms 18 ms 18 ms 62.YYY.YYY.YYY 3 62.YYY.YYY.YYY reports: Destination host unreachable.
I think it is because the VPN map doesn't define this network, does it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2018 07:20 AM
this article doesn't include any information about routing configuration moreover it has a wrong ACL. Here is a part my working config:
ISR 886 VA:
! crypto ikev2 proposal L2L-Prop encryption 3des integrity sha1 group 2 5 ! crypto ikev2 policy L2L-Pol proposal L2L-Prop ! crypto ikev2 keyring L2L-Keyring peer vpn address 187.XXX.XXX.XX1 pre-shared-key local ********* pre-shared-key remote ********* ! crypto ikev2 profile L2L-Prof match identity remote address 187.XXX.XXX.XX1 255.255.255.255 identity local key-id S2S-IKEv2 authentication remote pre-share authentication local pre-share keyring local L2L-Keyring ! crypto ipsec transform-set ESP-AES-SHA esp-aes esp-sha-hmac mode tunnel ! crypto map vpn 10 ipsec-isakmp set peer 187.XXX.XXX.XX1 set transform-set ESP-AES-SHA set ikev2-profile L2L-Prof match address vpn ! interface Dialer0 crypto map vpn ! ip route 10.255.10.0 255.255.255.0 187.XXX.XXX.XX1 ! ip access-list extended vpn permit ip 10.254.1.0 0.0.0.255 10.255.10.0 0.0.0.255 ! access-list 101 deny ip 10.254.1.0 0.0.0.255 10.255.10.0 0.0.0.255 access-list 101 permit ip 10.254.1.0 0.0.0.255 any
ASA 5510:
interface Ethernet0/0 duplex full nameif WAN security-level 0 ip address 187.XXX.XXX.XX1 255.255.255.248 ! interface Ethernet0/1 duplex full nameif LAN-MSP security-level 100 ip address 10.255.10.99 255.255.255.0 ! object network LAN-MSP subnet 10.255.10.0 255.255.255.0 object network OFFICE subnet 10.254.1.0 255.255.255.0 access-list vpn extended permit ip 10.255.10.0 255.255.255.0 10.254.1.0 255.255.255.0 nat (LAN-MSP,any) source static LAN-MSP LAN-MSP destination static OFFICE OFFICE ! crypto ipsec ikev2 ipsec-proposal ESP-AES-SHA protocol esp encryption aes protocol esp integrity sha-1 crypto ipsec security-association pmtu-aging infinite crypto dynamic-map dmap 1 match address vpn crypto dynamic-map dmap 1 set ikev2 ipsec-proposal ESP-AES-SHA crypto map vpn 1 ipsec-isakmp dynamic dmap crypto map vpn interface WAN crypto ca trustpool policy crypto ikev2 policy 1 encryption 3des integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 enable WAN group-policy Site-to-Site internal group-policy Site-to-Site attributes vpn-tunnel-protocol ikev2 tunnel-group S2S-IKEv2 type ipsec-l2l tunnel-group S2S-IKEv2 general-attributes default-group-policy Site-to-Site tunnel-group S2S-IKEv2 ipsec-attributes ikev2 remote-authentication pre-shared-key ******* ikev2 local-authentication pre-shared-key *******
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide