- Cisco Community
- Technology and Support
- Security
- VPN
- Making remote web server internet accessible over Site to Site VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2013 08:26 PM
We have two test site locations which are connected by an IPSEC site to site VPN tunnel across the internet (homed on an ASA at each site). We are attempting to setup an environment to test two web applications running side by side. Both of the web servers are running at Test Site 1. We only have single public IP address available at each site.
In order to overcome the single public IP address limitation at site 1, we are trying to setup ACL and NAT rules to have Site 2 accept the traffic coming from the internet and send it over the site to site tunnel. So Web Server 1 would accept internet traffic from ASA 1, and Web Server 2 would accept traffic from ASA 2 at the other site. Here is a network diagram:
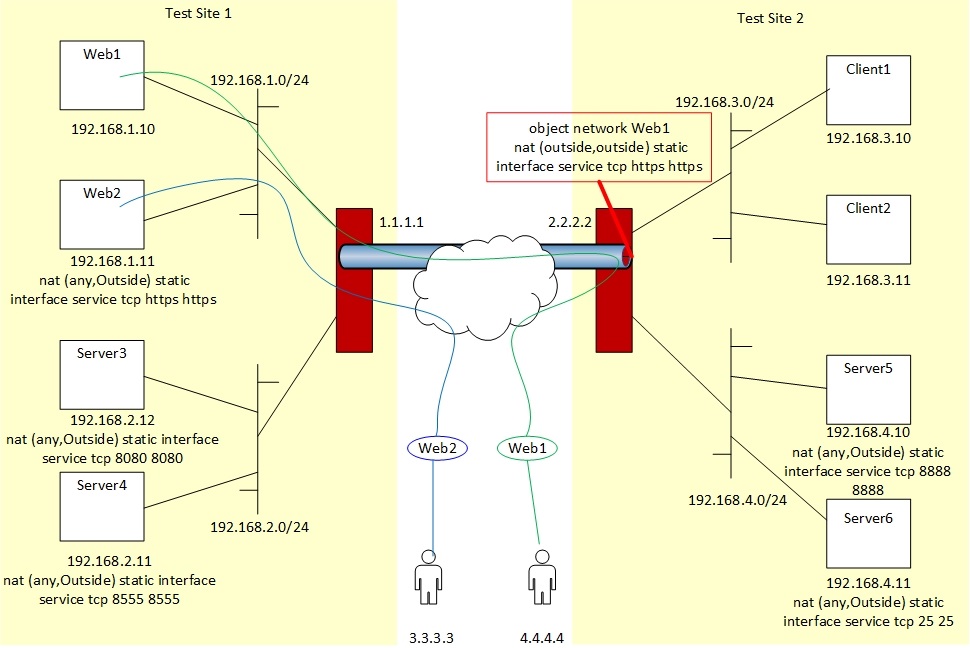
We are having trouble getting this setup to work correctly. Please note that clients on the 192.168.3.0/24 network are able to access Web1 and Web2 servers. This issue seems to be due to our NAT setup. Here is the type of error we are seeing on both firewalls:
Asymmetric NAT rules matched for forward and reverse flows; Connection for tcp src outside:4.4.4.4/443 dst outside:192.168.1.10/443 denied due to NAT reverse path failure
Our situation seems similar to this post: https://supportforums.cisco.com/thread/2242230
Any help would be much appreciated.
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2013 08:21 AM
Hi,
What Karsten said above is true. While this is possible and will work, it also means that the setup is a bit more complex to manage. I have not done such setups in a real life network environment and have always used extra public IP addresses on the local site where a server is hosted.
If you still want to go ahead with this then here are some things to consider and configurations that you will need.
First off it seems to me that the other server will be hosted through the local Site 1 so a simple Static PAT (Port Forward) should handle Site 1.
object network WEB-HTTP
host 192.168.1.10
nat (inside,outside) static interface service tcp 443 443
And if you need TCP/80 also then you will need
object network WEB-HTTPS
host 192.168.1.10
nat (inside,outside) static interface service tcp 80 80
Now, Site 2 will naturally be a bit different as the server is hosted at Site 1 and the public IP address used to publish the server to the external network is located at Site 2.
You will essentially need to do a NAT configuration that both does Dynamic PAT for the source addresses of the connection to your Web Server 2 but also does the Static PAT (Port Forward) for the actual Web Server 2 IP address. Furthermore you will have to define the Encryption Domain on both Site 1 and Site 2 to match this new addition to the L2L VPN connection.
Unless ofcourse you use an IP address existing on the Encryption Domain in the Dynamic PAT translation for the source address. In that case no changes to L2L VPN would be needed. I will use that in the below example.
The NAT configuration might look something like this
object service WWW
service tcp destination eq 80
object service HTTPS
service tcp destination eq 443
object network SOURCE-PAT-IP
host 192.168.3.254
object network WEB-SERVER-2-SITE1
host 192.168.1.11
nat (outside,outside) 1 source dynamic any SOURCE-PAT-IP destination static interface WEB-SERVER-2-SITE1 service WWW WWW
nat (outside,outside) 2 source dynamic any SOURCE-PAT-IP destination static interface WEB-SERVER-2-SITE1 service HTTPS HTTPS
So essentially the above NAT configurations should ake "any" traffic coming from behind "outside" interface destined to "outside" "interface" IP address and translate the source address to "SOURCE-PAT-IP" and untranslate the destination to "WEB-SERVER-2-SITE1".
Make sure that the IP address chosen (in this case 192.168.3.254) is not used on any device. If it is then replace it with something that is not used currently in the network. Otherwise configure an IP address from some other subnet and include that in the L2L VPN configurations on both sites.
Unless you already have it, you would also need this configuration command to enable the traffic to take an U-turn/Hairpin on the "outside" interface of Site 2 ASA
same-security-traffic permit intra-interface
Hope this helps
Please do remember to mark a reply as the correct answer if it answered your question.
Feel free to ask more if needed.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2013 11:36 PM
long time ago I had a similar setup where a server located at a branch-office had to be accessed through the internet-connection at the HQ. In the end it worked, but the solution was hard to maintain and my standpoint is clearly "don't do that!". Rule of thumb: If you can't explain your solution at 2:30am to a TAC-engineer, look for a simpler solution!
The three ways that are better solutions:
1) tell your ISP that you need more IPs.
2) place the server in site2.
3) send all web-traffic to a reverse-proxy, which in turn sends the traffic to the right server.
If you still want to do it your way, it seems that there is at least a NAT missing.
Traffic for Web1 needs the source to be translated so that it can be sent through the tunnel. You could use your public IP of the ASA (2.2.2.2) for that.
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2013 08:21 AM
Hi,
What Karsten said above is true. While this is possible and will work, it also means that the setup is a bit more complex to manage. I have not done such setups in a real life network environment and have always used extra public IP addresses on the local site where a server is hosted.
If you still want to go ahead with this then here are some things to consider and configurations that you will need.
First off it seems to me that the other server will be hosted through the local Site 1 so a simple Static PAT (Port Forward) should handle Site 1.
object network WEB-HTTP
host 192.168.1.10
nat (inside,outside) static interface service tcp 443 443
And if you need TCP/80 also then you will need
object network WEB-HTTPS
host 192.168.1.10
nat (inside,outside) static interface service tcp 80 80
Now, Site 2 will naturally be a bit different as the server is hosted at Site 1 and the public IP address used to publish the server to the external network is located at Site 2.
You will essentially need to do a NAT configuration that both does Dynamic PAT for the source addresses of the connection to your Web Server 2 but also does the Static PAT (Port Forward) for the actual Web Server 2 IP address. Furthermore you will have to define the Encryption Domain on both Site 1 and Site 2 to match this new addition to the L2L VPN connection.
Unless ofcourse you use an IP address existing on the Encryption Domain in the Dynamic PAT translation for the source address. In that case no changes to L2L VPN would be needed. I will use that in the below example.
The NAT configuration might look something like this
object service WWW
service tcp destination eq 80
object service HTTPS
service tcp destination eq 443
object network SOURCE-PAT-IP
host 192.168.3.254
object network WEB-SERVER-2-SITE1
host 192.168.1.11
nat (outside,outside) 1 source dynamic any SOURCE-PAT-IP destination static interface WEB-SERVER-2-SITE1 service WWW WWW
nat (outside,outside) 2 source dynamic any SOURCE-PAT-IP destination static interface WEB-SERVER-2-SITE1 service HTTPS HTTPS
So essentially the above NAT configurations should ake "any" traffic coming from behind "outside" interface destined to "outside" "interface" IP address and translate the source address to "SOURCE-PAT-IP" and untranslate the destination to "WEB-SERVER-2-SITE1".
Make sure that the IP address chosen (in this case 192.168.3.254) is not used on any device. If it is then replace it with something that is not used currently in the network. Otherwise configure an IP address from some other subnet and include that in the L2L VPN configurations on both sites.
Unless you already have it, you would also need this configuration command to enable the traffic to take an U-turn/Hairpin on the "outside" interface of Site 2 ASA
same-security-traffic permit intra-interface
Hope this helps
Please do remember to mark a reply as the correct answer if it answered your question.
Feel free to ask more if needed.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2013 08:25 AM
Also,
I noticed that in your post you mention Web 1 would be hosted through ASA1 and Web 2 through ASA2. The picture attached again would hint the situation is otherwise? So take that into consideration with the above configurations.
I have done them considering that Site 1 will have simple Static PAT for Web 1 and Site 2 will have more special NAT configurations for Web 2
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2013 11:04 AM
Jouni,
This is working perfectly. Thanks for your help with this! Your explanation was very clear. Never had to configure NATs this way before. Totally agree that this is not best practice and not recomended for production use. We are only using this setup to test something in regards to our web servers.
Thanks again!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



