- Cisco Community
- Technology and Support
- Security
- VPN
- Re: No internet access whilst connected to Cisco VPN client
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2010 06:47 AM
Hi.
We can’t browse the internet whilst our Cisco VPN client (v5.0.06.0160) is connected (to a Pix 515 firewall at a remote site). Initially we couldn’t connect to our LAN either so we followed these instructions to set up split tunnelling on the remote Pix.
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080702992.shtml
Specifically
1. Choose Configuration > VPN > General > Group Policy and select the Group Policy that you wish to enable local LAN access in. Then click Edit.
2. Choose the Client Configuration tab.
3. Uncheck the Inherit box for Split Tunnel Policy and chose Exclude Network List Below.
4. Uncheck the Inherit box for Split Tunnel Network List and then click Manage in order to launch the ACL Manager.
5. Within the ACL Manager choose Add > Add ACL...
6. in order to create a new access list.
7. Provide a name for the ACL and click OK.
8. Once the ACL is created, choose Add > Add ACE... in order to add an Access Control Entry (ACE).
9. Define the ACE that corresponds to the local LAN of the client.
a. Choose Permit.
b. Choose an IP Address of 0.0.0.0
c. Choose a Netmask of 255.255.255.255.
d. (Optional) Provide a description.
10. Click OK.
11. Click OK in order to exit the ACL Manager.
12. Be sure that the ACL you just created is selected for Split Tunnel Network List.
13. Click OK in order to return to the Group Policy configuration.
14. Click Apply and then Send (if required) in order to send the commands to the ASA.
This works fine except that our LAN reside on 2 networks (128.6.0.0/16 and 172.28.0.0/16) at opposite ends of a 10Mb dedicated link and the above config only gave us access to the network from which we made the VPN connection. As a result we changed 9.b. above, substituting 0.0.0.0/32 with both our network ranges and now we can access the remote network and our local networks when the VPN is connected but not the internet.
Can anyone else tell me what I need to add to get the internet as well? I sould point out that the VPN policy is giving out the correct IPs for the DNS servers here so I dont think it's a DNS issue.
Thanks
Rex
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2010 08:03 AM
For split-tunneling to work the group-policy should have an ACL that specifies traffic to be included/protected.
group-policy RFC-MurrayPark attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value acl_mdc_mim-remote_split_tunnel
So, the above is correct... but the ACL should specify the traffic to be protected only (all traffic not included in this ACL will not be sent through the tunnel).
Federico.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2010 06:55 AM
Hi Rex,
Normally when you loose internet when connected with the VPN client is because split-tunneling is not configured.
You can choose from allowing the clients to have their own local internet connection or to send all traffic to the PIX (and reroute the traffic back to the internet).
If you want split-tunneling, you need to check the group-policy applied to the VPN clients and make sure that split-tunneling is configured (and only including the networks that you should reach through the tunnel).
Please post this:
sh run group-policy
sh run access-list NAME --> change name for the name of the ACL showing under the split-tunneling.
Federico.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2010 07:50 AM
Hi Federico
Thanks for the reply. Results as follows. The group policy we are using is RFC-MurrayPark. Whilst VPN is connected we can access LAN-RangersFC, 172.28.0.0 and the remote network but not the internet.
sh run group-policy
group-policy RFC-MurrayPark internal
group-policy RFC-MurrayPark attributes
dns-server value 128.6.100.42 128.6.100.31
vpn-idle-timeout 300
split-tunnel-policy excludespecified
split-tunnel-network-list value RFC_Lan_Access
default-domain value mih.co.uk
group-policy mih-remote internal
group-policy mih-remote attributes
dns-server value 10.10.29.12 10.10.29.13
vpn-idle-timeout 600
split-tunnel-policy tunnelspecified
split-tunnel-network-list value acl_mdc_mim-remote_split_tunnel
default-domain value mih.co.uk
group-policy MS_Access internal
sh run access-list RFC_Lan_Access
access-list RFC_Lan_Access remark RFC
access-list RFC_Lan_Access standard permit LAN-RangersFC 255.255.0.0
access-list RFC_Lan_Access remark MP
access-list RFC_Lan_Access standard permit 172.28.0.0 255.255.0.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2010 08:03 AM
For split-tunneling to work the group-policy should have an ACL that specifies traffic to be included/protected.
group-policy RFC-MurrayPark attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value acl_mdc_mim-remote_split_tunnel
So, the above is correct... but the ACL should specify the traffic to be protected only (all traffic not included in this ACL will not be sent through the tunnel).
Federico.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2010 07:12 AM
Thanks, worked a treat (just tunneled the remote network)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 11:56 AM
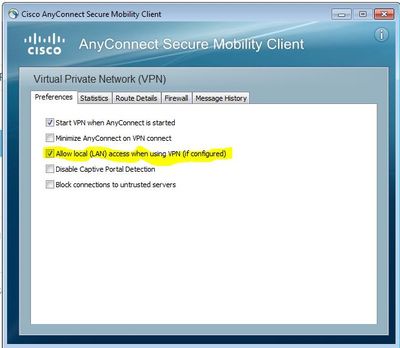
If you are using Cisco VPN software as Cisco AnyConnect Secure Mobility Client
Cisco AnyConnect Secure Mobility Client-> Settings -> Preferences -> Select Allow Local (LAN) access when using VPN ( if configured). Then reconnect the VPN. It should fix the problem.
You will have internet access while connected to Cisco VPN Client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2022 02:58 AM
Sorry to Jump in on an old thread. But we are having the same issues with our connection into the office.
We need to be able to access several PC's on the work network as well as be able to run internet dependant applications on the laptop connecting into work via the Cisco AnyConnect Secure Mobility Client.
I have been through all the related threads on this issue but nothing is working.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: