- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Site to Site VPN with Full Internet tunnel one Site has a static I
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site to Site VPN with Full Internet tunnel one Site has a static IP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 02:18 AM - edited 01-23-2024 04:49 AM
Dear All Members,
I am trying to set up the 819 4G Router as a VPN Client (Router) with the purpose of full internet tunnelling.
The goal here is the Remote users behind the 4G Router when he travels overseas and connect to any 4g network and when he does whats my IP? He gets the static IP of the Home Network 193.237.X.X----.->
Basically, I am trying to set up a network similar to EXPRESS VPN or BearVPN
I have one static IP at home, but the remote router may sometimes have a CGNAT IP or a Dynamic IP address?
I have googled and searched this forum to see whats the best configuration method for it. Please help me with the Home Router and Remote router configuration that makes it work.
Currently I have the 3945E Home router has Anyconnect with full tunnel that works with anyconnect endpoints (e.g. iPhone , Android , Windows PC) but not a router
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2024 06:53 AM
HUB-HOSTNAME#show ip route 192.168.100.253 longer-prefixes
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 90.247.64.1 to network 0.0.0.0
D 192.168.100.0/24 [90/26882560] via 172.16.0.2, 10:11:45, Virtual-Access
In Spoke
R2_Router#show ip route 192.168.100.253 lo
R2_Router#show ip route 192.168.100.253 longer-prefixes
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 172.16.0.1 to network 0.0.0.0
192.168.100.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.100.0/24 is directly connected, Vlan1
L 192.168.100.253/32 is directly connected, Vlan1
R2_Router#
R2_Router#
R2_Router#
R2_Router#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2024 06:59 AM
both show exact same
hub know this subnet from VTI
and Spoke via direct connect vlan1
the last thing is check the ACL in hub are you use any ACL in hub prevent ping ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2024 07:07 AM
@MHM Cisco World THATS ALL THE ACLS that I have on the HUB
ip local pool SSLVPN_POOL 192.168.10.1 192.168.10.200
ip local pool DSL_ACCESSLIST 142.202.YY.51 142.202.YY.99
ip forward-protocol nd
!
ip http server
ip http access-class 23
ip http authentication aaa
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
no ip nat service sip tcp port 5060
no ip nat service sip udp port 5060
ip nat inside source list DSL_ACCESSLIST interface Dialer1 overload
ip nat inside source static tcp 142.202.YY.EXPRESSWAY 8443 interface Dialer1 8443
ip nat inside source static tcp 142.202.YY.EXPRESSWAY 5061 interface Dialer1 5061
ip nat inside source static tcp 142.202.YY.EXPRESSWAY 5222 interface Dialer1 5222
ip nat inside source static udp 142.202.YY.EXPRESSWAY 3478 interface Dialer1 3478
ip nat inside source static tcp 142.202.YY.EXPRESSWAY 3478 interface Dialer1 3478
ip nat inside source static tcp 142.202.YY.EXPRESSWAY 5060 interface Dialer1 5060
ip nat inside source static udp 142.202.YY.EXPRESSWAY 5060 interface Dialer1 5060
ip nat inside source static tcp 142.202.YY.HOST 3389 interface Dialer1 3389
ip nat inside source static tcp 142.202.YY.HOST2 3389 62.31.221.93 3389 extendable
ip route 0.0.0.0 0.0.0.0 Dialer1
ip ssh rsa keypair-name KEYPAIR
ip ssh version 2
!
ip access-list extended DSL_ACCESSLIST
permit ip 142.202.YY.0 0.0.0.255 any
permit ip 192.168.20.0 0.0.0.255 any
permit ip 142.202.ZZ.0 0.0.0.255 any
permit ip 192.168.10.0 0.0.0.255 any
permit ip 192.168.1.0 0.0.0.255 any
permit ip 192.168.100.0 0.0.0.255 any
permit ip any any
!
!
ip prefix-list REDIST_STATIC seq 5 permit 0.0.0.0/0
!
nls resp-timeout 1
cpd cr-id 1
route-map REDIST_STATIC permit 10
match ip address prefix-list REDIST_STATIC
!
!
access-list 1 permit 192.168.10.0 0.0.0.255
access-list 1 permit 142.202.0.0 0.0.255.255
access-list 1 permit any
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2024 02:52 AM
@MHM Cisco World Good morning and sorry to bother you so what do you think is the problem now ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2024 10:33 PM
Hi Friend
the ACL 1 use for what
other ACL I know for what it use but ACL 1 I dont see where you use it
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2024 10:38 PM
@MHM Cisco World ACL1 is for anyconnect VPN. I do have ANYCOMNECT VPN installed , its working perfectly and tunneling the Internet traffic as well
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2024 02:20 AM
@MHM Cisco World I am sorry to disturb you and thank you for everything? Any updates from your end?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 06:06 AM
@MHM Cisco World Any updates please? Could you please share your LAB show run??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 10:14 AM
To achieve your goal of setting up a 4G router as a VPN client with full internet tunneling, you'll need to configure both the home router and the remote router appropriately. Here's a general guide on how you can configure them:
Home Router Configuration:
- Ensure that your home router (3945E) supports VPN client functionality. You'll likely need to configure it to establish a VPN tunnel to a VPN server.
- Set up the VPN client on your home router to connect to a VPN server. This server should have a static IP address or domain name that your remote router can connect to.
- Configure the VPN client on your home router to use full tunneling mode, which will route all traffic from the remote router through the VPN tunnel.
- Make sure that the VPN client is configured to allow traffic from the remote router's subnet to pass through the VPN tunnel.
Remote Router Configuration:
- Configure your 4G router to act as a VPN client, similar to the home router.
- Set up the VPN client on the remote router to connect to the VPN server running on your home router.
- If the remote router may sometimes have a CGNAT IP or a dynamic IP address, consider using a dynamic DNS (DDNS) service to associate a domain name with the remote router's IP address. This way, even if the IP address changes, the VPN client can still connect to the VPN server using the domain name.
- Ensure that the remote router's VPN client is configured to use full tunneling mode to route all traffic through the VPN tunnel.
Testing and Troubleshooting:
- Once both routers are configured, test the VPN connection to ensure that it's working correctly. You should be able to access resources on your home network from devices connected to the remote router.
- If you encounter any issues, check the VPN client logs on both routers for error messages that can help diagnose the problem.
- Make sure that any firewall or security settings on both routers allow VPN traffic to pass through.
Keep in mind that the specific steps for configuring the routers may vary depending on the make and model of the routers and the VPN software you're using. Consult the documentation provided by the router manufacturer and the VPN software for detailed instructions on how to set up VPN client functionality.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2024 09:41 AM
@jacquelinebrock Thank you very much for your contribution. I have anyconnect VPN part 1 is working perfectly and yes I have a static IP address too. The remote clients are Anyconnect VPN Client either (Android ,iOS , Windows or Macbook) all that is working perfectly for me.
Part 2 that's where I have the problem to configure the remote 4g router as a VPN client that's where my dilemma is. I have worked @MHM Cisco World and its nearly there but remote hosts are not getting internet connectivity .
Your guidelines are perfect but I need the actual configuration steps to implement it.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2024 03:14 AM
deep investigate after you ask me lab
can you remove
tunnel mode ipsec ipv4 <<- from spoke and hub and check again ping
same config as before except remove the above
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2024 10:51 AM
@MHM Cisco World Thank you very much again for coming back
I have looked at the hub and spoke now, and I don't have that statement anywhere
"tunnel mode ipsec ipv4" so Its not there already
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2024 12:00 PM
Hello @heshamcentrino1. It's great to hear that the Anyconnect VPN Client setup is working smoothly for you. Now, let's focus on configuring the remote 4G router as a VPN client to ensure internet connectivity for remote hosts
To proceed with the configuration steps for the remote 4G router, we need to delve into the specifics of your router model and the VPN software you're using. Since you mentioned your familiarity with the Cisco environment, we can tailor the configuration steps accordingly.
Could you please provide the make and model of the 4G router you're using? Additionally, let us know which VPN software or protocol you intend to utilize for establishing the VPN connection between the remote 4G router and your home router. This information will enable us to tailor the configuration steps accurately to your setup.
Once we have these details, we can proceed with outlining the configuration steps for setting up the remote 4G router as a VPN client. Feel free to ask any questions or provide further details to assist you better.
Looking forward to your response!
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2024 08:02 PM
@jacquelinebrock Thank you very much for your message. Sorry for my late response. I was very sick and had infection that's why I wasn't able to respond on timely manner. I apologise for that. I appreciate all your help
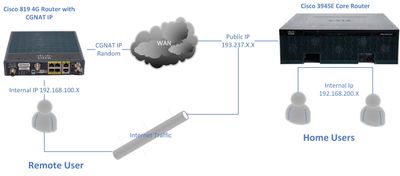
The 4G router that I am using is C819G-4G-G-K9 V01 that's my spoke and my hub is 3945E with Static IP. The initial VISIO diagram exhibits my setup and here you are attached again my topology.
I have configured FLEXVPN between the Hub and Spoke. The VPN tunnel is up but I have the following problems.
1-No internet at the spoke but when tracerouting or show ip route it the traffic is routed properly through the tunnel to the ISP. Also when pinging 4.2.2.2 it does ping successfully via the hub
2- Hosts at the spoke can't ping hosts at the hub but they can ping the VLAN gateway only and vice versa from the hub to spoke.
My configuration is shared previously in the previous posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2024 07:55 PM
@MHM Cisco World and @jacquelinebrock any updates please??
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide