- Cisco Community
- Technology and Support
- Networking
- Routing
- How to: NAT public IP within Network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to: NAT public IP within Network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2017 08:18 AM - edited 03-05-2019 09:11 AM
Hey Cisco Community:
I have a simple question. Can I NAT just my guest wireless network, whose VLAN gateway sits on my L3 switches (HSRP), onto a public IP and not have it translated again by my second NAT, which sits on the last hop out of my network? I have CCNA training, but it's been a while since I did NAT.
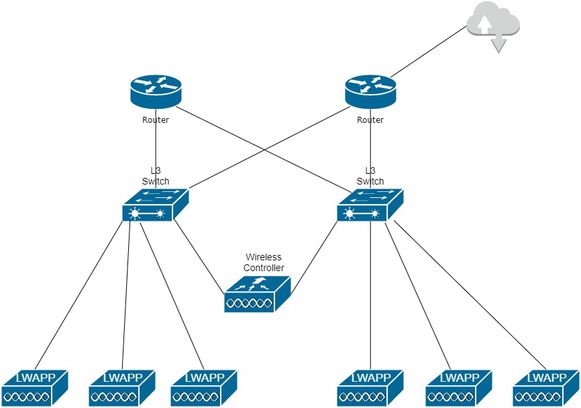
Thank you for your time and consideration.
-Mike
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2017 08:28 AM
Hi there,
Of course you can NAT a packet as much as you like, however I belive the problem you will encounter is that your L3 switch does not support it. AFAIK the 6500 is the only L3 switch which can do NAT.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2017 08:37 AM
Great point about the L3 Switch not being able to NAT (I'm using 3560's). So, I'm left with the option of NATing on the router. So would the most advised network design require forwarding traffic to a Vlan on the router for translation?
Example: The following sequence would take place:
1. Forward Guest traffic to Vlan X on router via static route.
2. Translate traffic on Vlan X to public IP.
3. Forward traffic on Vlan X out of the network.
Is that a correct assumption?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2017 08:45 AM
Based on the topology you have provided, the only change you would need to make is to include the source subnet (the guest WLAN) to the ACL which is used by the dynamic NAT statement on your routers.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2017 09:39 AM
Hi Seb:
In my initial scenario, I alluded to the fact that I'm using two public IP's. One public IP for my guest WLAN y.y.y.y and another public IP for the rest of my network x.x.x.x. If I append my ACL for my dynamic NAT to include traffic from my guest WLAN, I believe that all network traffic will be forwarded as x.x.x.x into the WAN.
I'm looking for a solution whereby I can forward all traffic out of my network through a single interface, but have one part of my network NAT'ed as x.x.x.x and segregate my guest WLAN onto y.y.y.y
Do you still believe your previous solution to be adequate?
Thanks,
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2017 12:13 AM
Looking at your diagram, does a single router have both ISP links attached? If that is the case it should have two NAT statements, so you would need to edit the NAT source ACL for the y.y.y.y WAN link to include your guest WLAN subnet. You will also need to configure Policy Based Routing to direct traffic from your Guest WLAN out of the second WAN link. If you have a BGP peering with your ISP you should also advertise the specific Guest WLAN prefix to the second ISP.
You could simplify the design a little, by placing the Guest WLAN and second ISP link in a seperate VRF, however without route leaking between VRFs you would lose the WAN redundancy you currently have.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 10:39 AM
I'll need another day to consider your solution. Thanks for your fast reply!
-Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2017 01:50 AM - edited 09-27-2017 01:53 AM
Hello
Only rtrs and high end swittches( 6500's +) is NAT supported.
Also your guest network should be totally segregated from you working LAN, it should have no way of reaching anything internally, it shouldnt even be routed on your L3 switches.
Your guest network should be layer 2 only upto the FW or wan router where it can get natted
res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 10:36 AM
I like the best practice solution of routing layer 2 up to Firewall or Forwarding router for guest traffic. Thank you for your suggestion.
-Mike
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
