- Cisco Community
- Technology and Support
- Security
- Web Security
- Cisco WSA ironport S170 bypass settings and proxy rules problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2018 09:15 AM - edited 03-08-2019 07:45 PM
Hello,
My WSA is on version 9.1.1-074 and I'm having a problem whenever I try to edit my Bypass Settings list or change a custom URL Categorie.
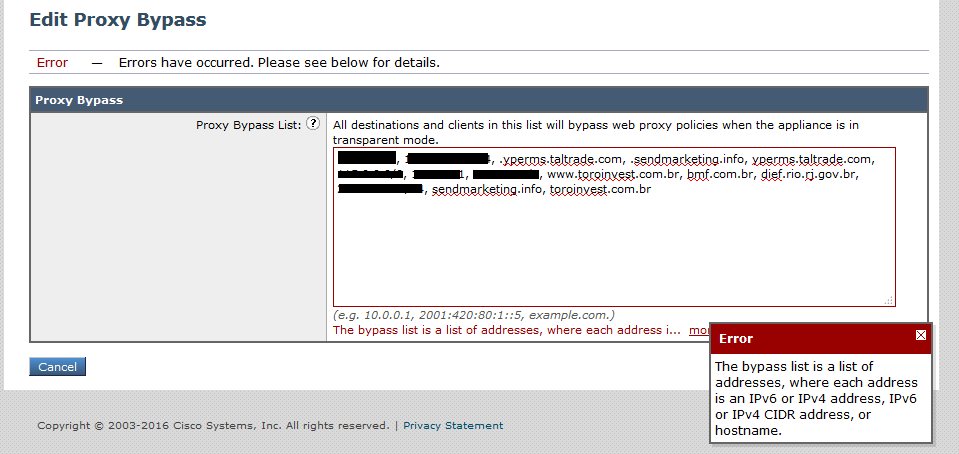
On my Bypass Settings, even if I don't edit NOTHING at all and just click "submit" after clicking on "Edit Proxy Bypass Settings" it gives me an Error like "The bypass list is a list of addresses, where each address is an IPv6 or IPv4 address, IPv6 or IPv4 CIDR address, or hostname.".
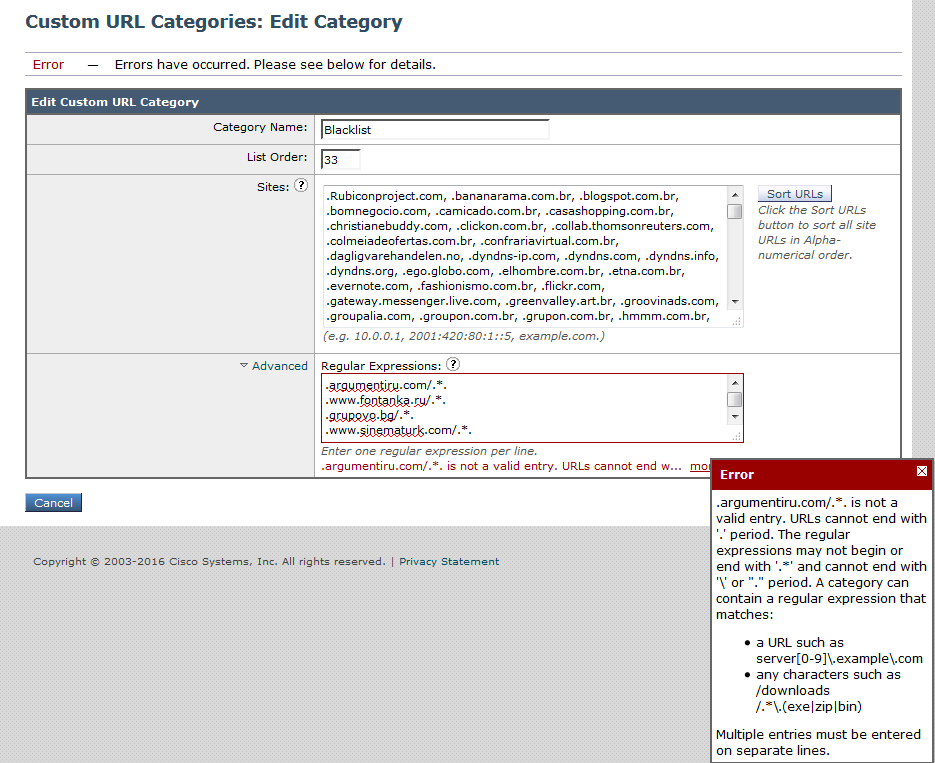
On my custom URL Categorie it's basically the same but the error says that the regular expression cannot end with "/.*.". I know that this sintax is not allowed any more, but I fail to understand how, even if this type of regex isn't allowed, it still is configured like so.
Is there any way that I can edit my custom URL categorie removing the error from all the lines where it appears, for example, removing the ".*." for something that will pretty much mean the same(match anything that comes after this domain) ?
Solved! Go to Solution.
- Labels:
-
Web Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2018 07:59 PM
Hi,
In regards to the loopback address, it is ok to remove it.
You can also has acl in your WCCP server to regulate the traffic, for example to not to redirect traffic to WSA if the destination IP address is the WSA IP address.
Below are some of WCCP examples:
For the regular expression, we do not have any automatic process to do that, however you can make the changes from the configuration file (xml file) it self and made the change then upload it back to the appliance.
Regarding to the upgrade to 9.1.3, i would suggest that you review the release note first to get more info about the versions. Below is the release note
https://www.cisco.com/c/dam/en/us/td/docs/security/wsa/wsa9-0/wsa9-1/WSA_9-1-x_Release_Notes.pdf
Hope this helps
Regards
Handy Putra
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2018 07:46 PM
Hi,
Starting version 9 and above we have made few changes on those area to rectify few issues and to make sure the setting is working as it should.
Regarding to the bypass setting, prior to this version we are allow to enter ".example.com" or "*.example.com", however in reality (real traffic) it will still not bypass using that configuration, thats why on version 9 and above we prevent that entry now.
The entries in bypass list takes the following forms:
- IP address
- CIDR address such as 10.1.1.0/24
- domain name such as example.com
- hostname such as crm.example.com
(It DOES NOT allow partial hostname such as .example.com, but example.com would match www.example.com if T1 interface is monitoring DNS queries)
In our current implementation of "proxy bypass", this feature only works under transparent deployment.
Meaning, if the HTTP request is explicitly forwarded into the proxy port, "proxy bypass" would not take effect.
Let's say you have example.com in your "proxy bypass" list, and T1 interface is not connected.
In this case, WSA would perform an explicit DNS lookup for example.com to update its internal cache,
requests going to and from example.com would be "bypassed". But requests going to and from www.example.com would NOT be "bypassed".
Next, if T1 interface is monitoring DNS traffic, any DNS queries with domain of example.com
(www.example.com, mail.example.com ...etc) will be snooped, and it's IP will be added into WSA's "proxy bypass" list.
As a result, HTTP requests to www.example.com WILL be able to bypass the proxy.
So, if you are only using
- an IP address
- a CIDR address such as 10.1.1.0/24
- a hostname(FQDN) such as crm.example.com
It is not required to use T1 interface to snoop DNS queries unless the hostname uses some sort of dynamic IP range. In this case, it is possible that the hostname resolution on the client is different than the hostname resolution on the WSA and the proxy bypass would not match.
For then regular expression in the Custom URL categories, having those at the end of the regex will be very expensive in term of resources usage and that will cause performance issue.
You will need to make the regular expression more define rather than apply all to matches any arbitrary string of characters which is very expensive in resource.
Regards
Handy Putra
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2018 04:26 AM
Hey Putra,
Thanks for your quick and informative response.
Our WSA is currently working on Transparent mode, so I think the Bypass Setting is actually working for the valid entries on the list.
As of my issue with the Bypass Settings, I've tried editing it and noticed that when I remove the loopback address and the invalid ".something.com" urls, it lets me submit it. I'm not sure why the loopback address was on the list, but is it ok for me to remove it?
We currently have 34 custom URL categories, and I noticed that almost all of them have this type of syntax on their regular expression field. Is there a way for me to remove all of those invalid entries automatically?
Our WSA is asking us to update the AsyncOS version to "AsyncOS 9.1.3 build 016" and I'm afraid that if we update it we'll have major issues because of the custom URL categories with the wrong syntax.
P.S.: I've just assumed this area on the company I work and since it's the first time I'm in contact with ironport, I apologize if I misunderstood something.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2018 07:59 PM
Hi,
In regards to the loopback address, it is ok to remove it.
You can also has acl in your WCCP server to regulate the traffic, for example to not to redirect traffic to WSA if the destination IP address is the WSA IP address.
Below are some of WCCP examples:
For the regular expression, we do not have any automatic process to do that, however you can make the changes from the configuration file (xml file) it self and made the change then upload it back to the appliance.
Regarding to the upgrade to 9.1.3, i would suggest that you review the release note first to get more info about the versions. Below is the release note
https://www.cisco.com/c/dam/en/us/td/docs/security/wsa/wsa9-0/wsa9-1/WSA_9-1-x_Release_Notes.pdf
Hope this helps
Regards
Handy Putra
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: